-
Posts
15 -
Joined
-
Last visited
Recent Profile Visitors
The recent visitors block is disabled and is not being shown to other users.
-

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Ducdanh Nguyen, virtually every adapter will work. I'm using DFRobot multiplexer v.1.0 (FT232R-based): https://wiki.dfrobot.com/Multi_USB_RS232_RS485_TTL_Converter__SKU_TEL0070_ -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
As I said above, there is no usb otg functionality. If you want shell as ordinary user - install any app which allows access to shell (I'm using "Admin hands" in local shell mode) on your tv box. In this mode 'su' refuses to escalate privileges. If you want root access, you should connect using uart (see my messages above). You will get access to u-boot and android console. There you can execute 'su' and it will give you root privileges. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Octavio Cuatrochio, you need root privileges to modify any partition at runtime. If you want to modify firmware, get update.zip to your PC, modify it, and flash using android's Settings->About->Local update. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Octavio Cuatrochio, your box is locked no more than others. ADB over USB doesn't work on all versions. su works only through uart console. Toothpick method is only for recovery from backup partition (so 'upgrade' is not really upgrade - it's reflashing from backup). What to check: 1. Check you haven't shorted Tx and Rx to +3.3V. bus (trace between two test points). 2. Are Gnd's of the usb converter and tv box connected? 3. You have some switches on usb converter - what it is for? I/O voltage select? 4. Make sure you open serial port on PC with 115200 8n1 settings without hardware or software flow control. 5. You've checked it while lines was free-floating or connected to usb converter? If last, make measurements without usb converter connected. About performance of Android and Armbian: idk. Current Android firmware is 32-bit. But, according to datasheet, Hi3798MV310 have 64-bit core. So, if you manage to create 64-bit build of Android or Armbian, I suppose it should have slightly better performance. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@AndroidNewbie, what kind of help do you expect to receive? @Ducdanh Nguyen, are you sure it was my modified update.zip (hint: open it with any archiver and see for file "wipedata.flag" - is it there?)? Are old settings and apps stays in place after flashing? Are update.zip located in root of sd card? If all answers is yes, then try to update using usb flash drive instead of sd card. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Ducdanh Nguyen, if you mean usb<->uart converter, virtually anything with cmos/ttl 3.3v. i/o levels (5v. probably is fine too) will work. Based on ch340 or pl2303 or cp2101 or some FTDI chips - all they should work. But don't use usb<->rs232 converters or COM port directly. If you talking about soldering some sort of connector to tv box board, then I can't suggest anything, except some straight separate pin. This test points are just separate pads and they don't suit any of connectors I familiar with. IMO better way is to solder thin flexible wires (preferably in PTFE or silicone insulation) to the board, and then solder any kind of connector to them. You need uart connected only if you wish to interact by it means with tv box. Through uart you can interact with u-boot bootloader, inspect kernel output and have access to shell console with 'su' enabled. But, just to simply boot tv box, you don't need uart. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Ducdanh Nguyen, about uart: just find someone with soldering skills - it's deal of 3 minutes to solder 3 wires. Screenshots: all them taken from one tv box. I've found recovery menu only once - when accidentally flashed update.zip with system and vendor partitions taken from other tv box (also HiSilicon-based). After flashing, something went wrong while starting Android, and box automatically rebooted to recovery. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Ducdanh Nguyen, I don't understand how you could use electrical (insulation?) tape to connect to test points... Nevertheless, all you need is a good electrical contact between wires and test points. Means has no matter. Beware: signal levels is 3.3V. Do not connect directly to RS232 interface! What about flashing my modified update.zip - don't worry. It doesn't alter partition table, bootloader and backup partition. If something goes wrong, or you just want original firmware back - just connect power while holding button near "A/V" jack. This will start reflashing using your original update.zip, located in backup partition. If you want to extract your original update.zip from backup partition, simplest way to do this is using uart. Connect uart to pc, boot tv box normally, open serial port on pc (115200/8/n/1), issue 'su' command, mount /backup and copy /backup/update.zip anywhere you want. About laptop - I don't understand, how it's related to this discussion... If you want to compile armbian using it - go ahead. It doesn't matter what cpu architecture or type of memory it uses. All you need is correct toolchain, which suits our tv box SoC. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
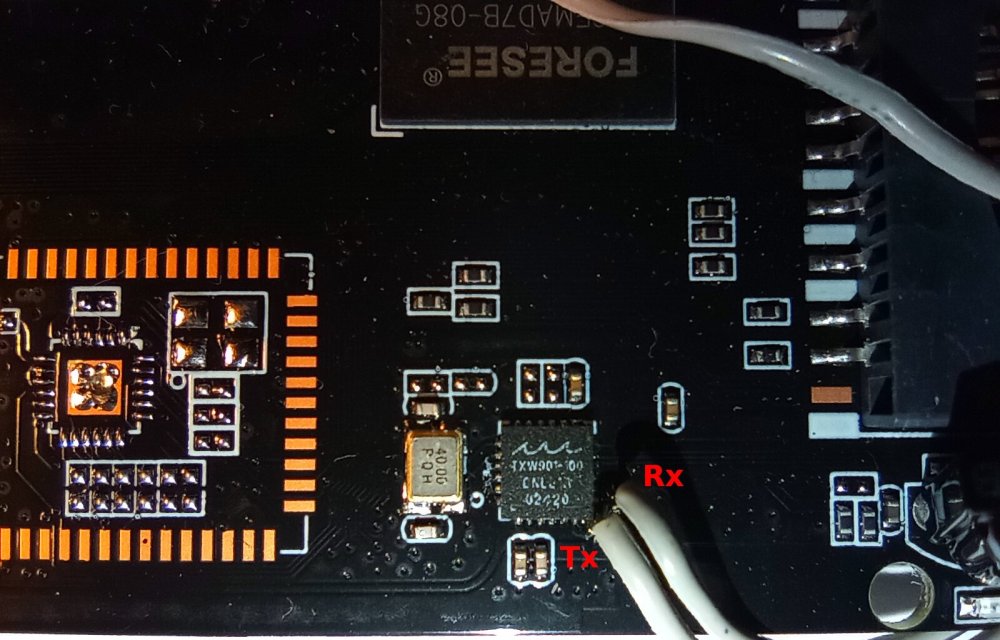
Yes, there are some updates. First of all I've found two uart interfaces. See attached photos. Two test points located on the bottom side of pcb is for SoC uart, and two near wifi interface is for TXW901 uart. Tx and Rx as on attached pics. Furthermore, AFAIR, powering on while holding SoC Rx low forces SoC to search for bootable usb flash drive. Second is my modified android (not armbian!) firmware v.0.2. You can download it using link in my message above. Changelog also there. Major changes: Google Play is working again, improved wifi stability. Third, there are Linux drivers available for TXW901 (Wifi interface). You can get it here: https://www.taixin-semi.com/Product?prouctSubClass=66 (registration is required, however, all that you need to register is valid e-mail). So, potentially, one could compile armbian image for this box (integrate wifi driver into armbian, obtain memory settings through SoC uart, configure and compile kernel and boot image). -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
If someone interested on this tv box: I've managed to download original firmware image (update.zip) from backup partition. Also I cleaned it from malware (at least I think so) and packed as modified update.zip. Files are located here: https://drive.google.com/drive/folders/1etPmH8ZG4UtPHI3Vf1U9MUHl5_gK_s-E Further info available here (in Russian): https://4pda.to/forum/index.php?showtopic=1016510&view=findpost&p=139209499 -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
@Ducdanh Nguyen, can you contact seller of your tv box and ask if they can provide firmware (or "firmware update") for it? -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
So i have found what's we dealing with: it is HiSilicon hi3798mv310. See attached proc_version and config.gz. Furthermore, I've installed eset nod32 antivirus on this box and it found some suspicious apps (see photo). I will send them to eset for more thorough analysis. Overall this news is "Not great, not terrible". @Ducdanh Nguyen, I think there is no pre-built armbian or other linux distro images for this chip. I did a brief google search and found only this SDK: https://github.com/JasonFreeLab/HiSTBLinuxV100R005C00SPC050 As it seems to me, you can compile it and get some clean linux for this box. Let us know if it works. BTW, author of this SDK recommend to burn it using HiTool. But HiTool uses UART (only?) to interact with chip, and we don't have UART wired on our board. There are seems to be option to upgrade it from usb flash, but how will this work - idk... Also, here is related discussion: What about debugging by usb - either through enabling Android "Debug over usb" function or booting with reset button pushed - I doubt it will work. Nevertheless, this tv box is usable for its direct purpose. All that should be done, is replacing heatsink and changing firmware to trusted one (without any trojans and viruses). BTW, funny fact: hi3798mv310 have only 3 USB interfaces, but on our board there are 4 USB connectors. LOL! I'm wondering if there any scam museum in the world? If any, this box will be a very interesting piece for them. config.gz proc_version -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
No, he's problem is much more simpler. He have JTAG and UART wired on his board, so it's not a problem to do virtually anything with his box. Are you sure? Have you successfully connected adb on PC to this tv box using usb cable? -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
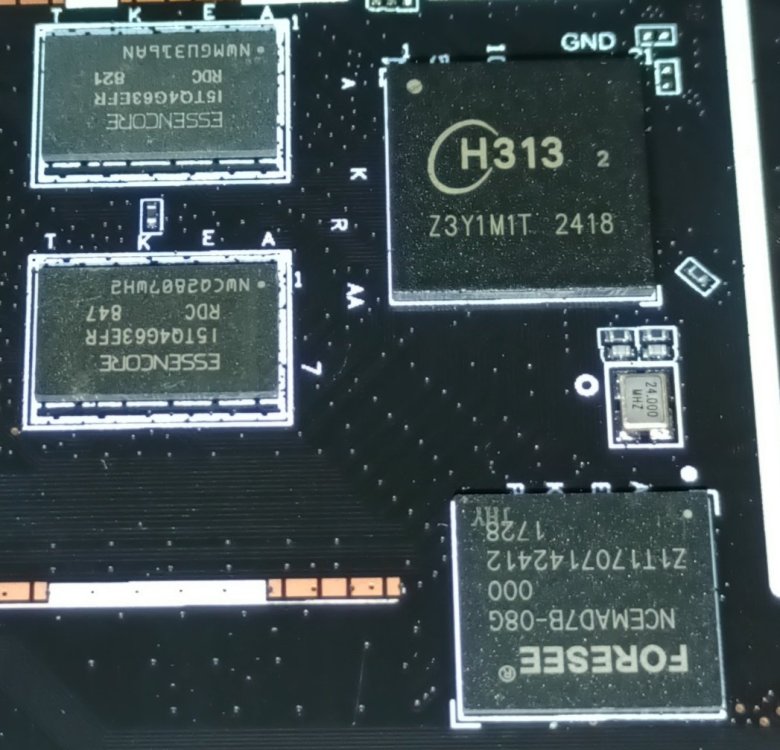
I've managed to pull out some system files out of it. Binaries is ELF 32-bit LSB executable, ARM, EABI5 version 1 (SYSV), so its not Allwinner H313. -

mxq pro 4k 5g allwinner h313 can't sd card boot
Sergey Lepeshkin replied to Ducdanh Nguyen's topic in Allwinner CPU Boxes
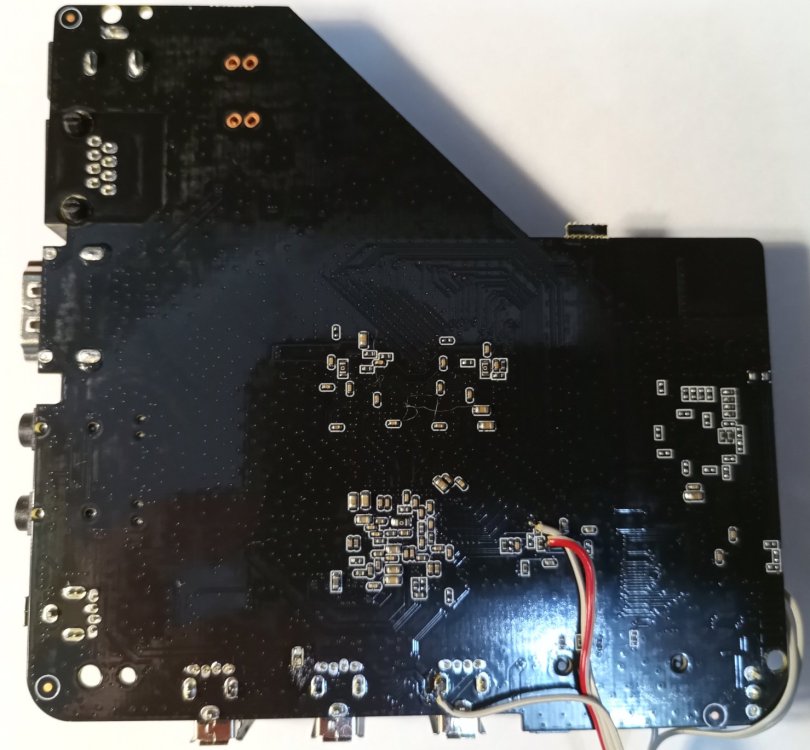
Hi! @Ducdanh Nguyen , which port have you used to connect it through adb? Those on the back side (where hdmi and power connectors located), or one of those on the right side (where sd card slot located)? Was it working in standard Android boot mode ("Debug over usb" enabled through "Developer settings") or somehow else? I also own such tv box and this is what I've found crawling web and playing with this device: 1. More PCB pics is here: https://4pda.to/forum/index.php?showtopic=1016510&view=findpost&p=136516719 2. "Heatsink" (just a small piece of thick aluminium foil) is bonded to SoC using 2-sided adhesive tape (I doubt it have good thermal conductivity). I recommend to replace it with more adequate heatsink. 3. SoC seems to be fake. It doesn't have Allwinner logo on it (there are 2 pics attached: one is ours, and one is genuine). 4. There is no AXP PMIC. Instead, there are 3 separate fixed step down converters. 5. There is no transformer in ethernet circuitry! Signals from jack goes directly to SoC. So be careful with static electricity while handling it's ethernet connection. 6. First button, located near "AV" jack, just resets tv box to factory defaults (if power switched on while it's pressed - and after that "update" screen with Chinese text on it will be shown). Purpose of second button (located near "S/PDIF" jack) is mystery for me. Can anyone suppose what it is for? 7. There are two exposed test points on the bottom side of pcb under SoC. Both tied through 10k resistors to +3.3V. After power-on, one of them seems to be some input (current between pin and gnd is about 3.3/10000=0.33mA), and other is definitely driven by something else (current is about 14mA and varying in both directions). I wonder if it's uart tx and rx pins - I'll see it with oscilloscope later. Anyway, shorting this test points together doesn't influence on boot process. 8. It's highly probable there is some backdoor (something like well-known Badbox 2.0). Original firmware exhibits some suspicious network behavior: just after factory reset, once it connected to network, it opens different connections to tcp port 12000 to hosts located in China. If I close outgoing traffic on firewall to tcp port 12000, after a while, it opens similar connections, but to port 9090 to different hosts. It seems to me it's trying to join some botnet. Furthermore, if you compare process list just after first (after factory reset) connection to network, and after it been connected for a while, you will find some new processes, which doesn't belong to Android and have strange names - I think it downloads something without asking user. Summary: this cheap tv box is a full scam. It seems to me manufacturer made all to prevent re-flashing of this device. But it will be very interesting to make something useful out of it.