zanzibar
Members-
Posts
15 -
Joined
-
Last visited
Content Type
Forums
Store
Crowdfunding
Applications
Events
Raffles
Community Map
Everything posted by zanzibar
-

[SOLVED][Odroid C2] Wifi AR9271 causes kernel crash after upgrade
zanzibar replied to zanzibar's topic in Amlogic meson
No more errors after upgrade to: 5.4.21-meson64 #20.02.3 SMP PREEMPT Fri Feb 21 17:46:54 CET 2020 aarch64 GNU/Linux Thanks. -

[SOLVED][Odroid C2] Wifi AR9271 causes kernel crash after upgrade
zanzibar replied to zanzibar's topic in Amlogic meson
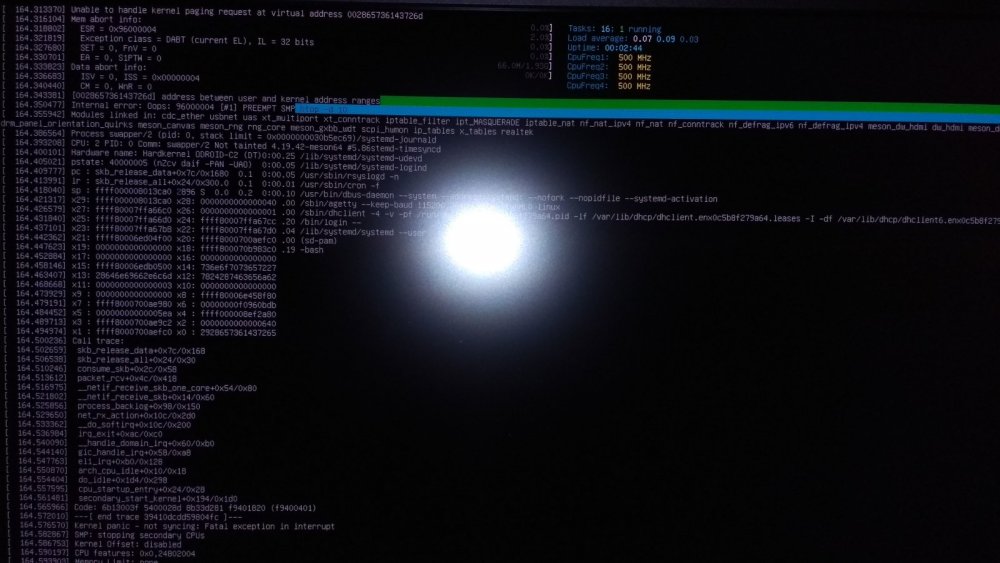
Hello, New bugs(kernel crash - odroid reboot) arrived after upgrade to 5.4.13-meson64 #20.02.2 SMP PREEMPT Mon Feb 17 23:18:02 CET 2020 aarch64 GNU/Linux ! After connect TP-Link TL-WN722N V1 USB WiFi dongle: Feb 18 15:05:08 rou2 kernel: usb 1-1.1: new high-speed USB device number 5 using dwc2 Feb 18 15:05:08 rou2 kernel: usb 1-1.1: New USB device found, idVendor=0cf3, idProduct=9271, bcdDevice= 1.08 Feb 18 15:05:08 rou2 kernel: usb 1-1.1: New USB device strings: Mfr=16, Product=32, SerialNumber=48 Feb 18 15:05:08 rou2 kernel: usb 1-1.1: Product: USB2.0 WLAN Feb 18 15:05:08 rou2 kernel: usb 1-1.1: Manufacturer: ATHEROS Feb 18 15:05:08 rou2 kernel: usb 1-1.1: SerialNumber: 12345 Feb 18 15:05:08 rou2 kernel: usb 1-1.1: ath9k_htc: Firmware ath9k_htc/htc_9271-1.4.0.fw requested Feb 18 15:05:08 rou2 kernel: usb 1-1.1: ath9k_htc: Transferred FW: ath9k_htc/htc_9271-1.4.0.fw, size: 51008 Feb 18 15:05:09 rou2 kernel: ath9k_htc 1-1.1:1.0: ath9k_htc: HTC initialized with 33 credits Feb 18 15:05:09 rou2 kernel: ath9k_htc 1-1.1:1.0: ath9k_htc: FW Version: 1.4 Feb 18 15:05:09 rou2 kernel: ath9k_htc 1-1.1:1.0: FW RMW support: On Feb 18 15:05:09 rou2 kernel: ath: EEPROM regdomain: 0x809c Feb 18 15:05:09 rou2 kernel: ath: EEPROM indicates we should expect a country code Feb 18 15:05:09 rou2 kernel: ath: doing EEPROM country->regdmn map search Feb 18 15:05:09 rou2 kernel: ath: country maps to regdmn code: 0x52 Feb 18 15:05:09 rou2 kernel: ath: Country alpha2 being used: CN Feb 18 15:05:09 rou2 kernel: ath: Regpair used: 0x52 Feb 18 15:05:09 rou2 kernel: ieee80211 phy1: Atheros AR9271 Rev:1 Feb 18 15:05:09 rou2 systemd-udevd[2227]: Using default interface naming scheme 'v240'. Feb 18 15:05:09 rou2 systemd[1]: Starting Load/Save RF Kill Switch Status... Feb 18 15:05:09 rou2 systemd-udevd[2227]: link_config: autonegotiation is unset or enabled, the speed and duplex are not writable. Feb 18 15:05:09 rou2 kernel: ath9k_htc 1-1.1:1.0 wlx54e6fc8d208e: renamed from wlan0 Feb 18 15:05:09 rou2 systemd[1]: Started Load/Save RF Kill Switch Status. Feb 18 15:05:09 rou2 systemd-udevd[2227]: Process '/sbin/iwconfig wlan0 power off' failed with exit code 250. Feb 18 15:05:09 rou2 systemd-udevd[2245]: Using default interface naming scheme 'v240'. Feb 18 15:05:09 rou2 systemd[1]: Found device AR9271 802.11n. Feb 18 15:05:09 rou2 systemd[1]: Started ifup for wlx54e6fc8d208e. Message from syslogd@localhost at Feb 18 15:05:10 ... kernel:[ 153.101849] Internal error: Oops: 96000004 [#1] PREEMPT SMP Message from syslogd@localhost at Feb 18 15:05:10 ... kernel:[ 153.291728] Code: b4000d56 b9402262 b9401020 11000400 (f8626ad8) Feb 18 15:05:09 rou2 wpa_supplicant[2262]: Successfully initialized wpa_supplicant Feb 18 15:05:10 rou2 kernel: Unable to handle kernel paging request at virtual address 00000010000002c0 Feb 18 15:05:10 rou2 kernel: Mem abort info: Feb 18 15:05:10 rou2 kernel: ESR = 0x96000004 Feb 18 15:05:10 rou2 kernel: EC = 0x25: DABT (current EL), IL = 32 bits Feb 18 15:05:10 rou2 kernel: SET = 0, FnV = 0 Feb 18 15:05:10 rou2 kernel: EA = 0, S1PTW = 0 Feb 18 15:05:10 rou2 kernel: Data abort info: Feb 18 15:05:10 rou2 kernel: ISV = 0, ISS = 0x00000004 Feb 18 15:05:10 rou2 kernel: CM = 0, WnR = 0 Feb 18 15:05:10 rou2 kernel: user pgtable: 4k pages, 48-bit VAs, pgdp=000000003ca51000 Feb 18 15:05:10 rou2 kernel: [00000010000002c0] pgd=0000000000000000 Feb 18 15:05:10 rou2 kernel: Internal error: Oops: 96000004 [#1] PREEMPT SMP Feb 18 15:05:10 rou2 kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 option huawei_cdc_ncm cdc_wdm usb_wwan cdc_ncm usbserial usbnet nf_log_ipv4 nf_log_common nft_limit cpufreq_powersave cpufreq_conservative xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink scpi_hwmon meson_rng rng_core meson_gxbb_wdt ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 18 15:05:10 rou2 kernel: CPU: 2 PID: 2262 Comm: wpa_supplicant Not tainted 5.4.13-meson64 #20.02.2 Feb 18 15:05:10 rou2 kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 18 15:05:10 rou2 kernel: pstate: 60000005 (nZCv daif -PAN -UAO) Feb 18 15:05:10 rou2 kernel: pc : __kmalloc+0xc0/0x278 Feb 18 15:05:10 rou2 kernel: lr : __kmalloc+0x44/0x278 Feb 18 15:05:10 rou2 kernel: sp : ffff800011b73cb0 Feb 18 15:05:10 rou2 kernel: x29: ffff800011b73cb0 x28: ffff00003cae3900 Feb 18 15:05:10 rou2 kernel: x27: ffff800010f8d270 x26: ffff800011b73e50 Feb 18 15:05:10 rou2 kernel: x25: ffff80001149cec0 x24: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x23: 0000000000021502 x22: 00000010000002c0 Feb 18 15:05:10 rou2 kernel: x21: ffff800010c5efe4 x20: 0000000000000dc0 Feb 18 15:05:10 rou2 kernel: x19: ffff000005303400 x18: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x17: 0000000000000000 x16: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x15: 0000000000000000 x14: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x13: 0000000000000000 x12: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x11: 0000000000000000 x10: 0000000000000000 Feb 18 15:05:10 rou2 kernel: x9 : 0000000000000000 x8 : 000000000002fb27 Feb 18 15:05:10 rou2 kernel: x7 : 0000000000000001 x6 : 0000000000000000 Feb 18 15:05:10 rou2 kernel: x5 : 0000000000000000 x4 : 0000000000000000 Feb 18 15:05:10 rou2 kernel: x3 : 0000000000000000 x2 : 0000000000000000 Feb 18 15:05:10 rou2 kernel: x1 : ffff00003cae3900 x0 : 0000000000000001 Feb 18 15:05:10 rou2 kernel: Call trace: Feb 18 15:05:10 rou2 kernel: __kmalloc+0xc0/0x278 Feb 18 15:05:10 rou2 kernel: sk_prot_alloc+0xa4/0x178 Feb 18 15:05:10 rou2 kernel: sk_alloc+0x34/0x198 Feb 18 15:05:10 rou2 kernel: packet_create+0x78/0x238 Feb 18 15:05:10 rou2 kernel: __sock_create+0x148/0x210 Feb 18 15:05:10 rou2 kernel: __sys_socket+0x5c/0xf0 Feb 18 15:05:10 rou2 kernel: __arm64_sys_socket+0x1c/0x28 Feb 18 15:05:10 rou2 kernel: el0_svc_common.constprop.2+0x88/0x150 Feb 18 15:05:10 rou2 kernel: el0_svc_handler+0x20/0x80 Feb 18 15:05:10 rou2 kernel: el0_svc+0x8/0xc Feb 18 15:05:10 rou2 kernel: Code: b4000d56 b9402262 b9401020 11000400 (f8626ad8) Feb 18 15:05:10 rou2 kernel: ---[ end trace 3d2076fdded0aff2 ]--- Feb 18 15:05:10 rou2 kernel: ------------[ cut here ]------------ Feb 18 15:05:10 rou2 kernel: kernel BUG at kernel/cgroup/cgroup.c:1421! After disconnect TP-Link TL-WN722N V1 USB WiFi dongle: Message from syslogd@localhost at Feb 18 15:02:21 ... kernel:[ 587.522450] Internal error: Oops: 96000004 [#1] PREEMPT SMP Feb 18 15:02:21 rou2 kernel: ------------[ cut here ]------------ Feb 18 15:02:21 rou2 kernel: refcount_t: underflow; use-after-free. Feb 18 15:02:21 rou2 kernel: WARNING: CPU: 0 PID: 0 at lib/refcount.c:190 refcount_sub_and_test_checked+0xd8/0xe0 Feb 18 15:02:21 rou2 kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 huawei_cdc_ncm cdc_wdm cdc_ncm option usbnet usb_wwan usbserial cpufreq_powersave cpufreq_conservative nf_log_ipv4 nf_log_common nft_limit xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core meson_gxbb_wdt scpi_hwmon ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 18 15:02:21 rou2 kernel: CPU: 0 PID: 0 Comm: swapper/0 Not tainted 5.4.13-meson64 #20.02.2 Feb 18 15:02:21 rou2 kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 18 15:02:21 rou2 kernel: pstate: 20000005 (nzCv daif -PAN -UAO) Feb 18 15:02:21 rou2 kernel: pc : refcount_sub_and_test_checked+0xd8/0xe0 Feb 18 15:02:21 rou2 kernel: lr : refcount_sub_and_test_checked+0xd8/0xe0 Feb 18 15:02:21 rou2 kernel: sp : ffff800010003cc0 Feb 18 15:02:21 rou2 kernel: x29: ffff800010003cc0 x28: ffff8000113eb1c0 Feb 18 15:02:21 rou2 kernel: x27: ffff8000113be6c0 x26: ffff8000113e18c8 Feb 18 15:02:21 rou2 kernel: x25: 0000000000000060 x24: 0000000000000002 Feb 18 15:02:21 rou2 kernel: x23: ffff0000411f30ee x22: 0000000000000001 Feb 18 15:02:21 rou2 kernel: x21: ffff0000412e7200 x20: 0000000000000078 Feb 18 15:02:21 rou2 kernel: x19: 0000000000000000 x18: ffff8000113fd000 Feb 18 15:02:21 rou2 kernel: x17: 0000000000000000 x16: 0000000000000000 Feb 18 15:02:21 rou2 kernel: x15: 00000000fffffff0 x14: ffff80001150c100 Feb 18 15:02:21 rou2 kernel: x13: 0000000000000000 x12: ffff80001150b000 Feb 18 15:02:21 rou2 kernel: x11: ffff8000113fd000 x10: ffff80001150b750 Feb 18 15:02:21 rou2 kernel: x9 : 0000000000000000 x8 : 0000000000000001 Feb 18 15:02:21 rou2 kernel: x7 : 000000000000016d x6 : ffff80001150b000 Feb 18 15:02:21 rou2 kernel: x5 : 0000000000000000 x4 : 0000000000000001 Feb 18 15:02:21 rou2 kernel: x3 : ffff8000113e4b50 x2 : 0000000000000004 Feb 18 15:02:21 rou2 kernel: x1 : b723429df7e70000 x0 : 0000000000000000 Feb 18 15:02:21 rou2 kernel: Call trace: Feb 18 15:02:21 rou2 kernel: refcount_sub_and_test_checked+0xd8/0xe0 Feb 18 15:02:21 rou2 kernel: __sock_wfree+0x20/0x48 Feb 18 15:02:21 rou2 kernel: skb_release_head_state+0x40/0xc0 Feb 18 15:02:21 rou2 kernel: skb_release_all+0x14/0x30 Feb 18 15:02:21 rou2 kernel: kfree_skb+0x2c/0x58 Feb 18 15:02:21 rou2 kernel: ath9k_htc_txcompletion_cb+0xcc/0xd8 [ath9k_htc] Feb 18 15:02:21 rou2 kernel: hif_usb_regout_cb+0x44/0x80 [ath9k_htc] Feb 18 15:02:21 rou2 kernel: __usb_hcd_giveback_urb+0x80/0xf8 Feb 18 15:02:21 rou2 kernel: usb_giveback_urb_bh+0xb0/0x108 Feb 18 15:02:21 rou2 kernel: tasklet_action_common.isra.15+0xc4/0x188 Feb 18 15:02:21 rou2 kernel: tasklet_hi_action+0x24/0x30 Feb 18 15:02:21 rou2 kernel: __do_softirq+0x124/0x240 Feb 18 15:02:21 rou2 kernel: irq_exit+0xb8/0xc8 Feb 18 15:02:21 rou2 kernel: __handle_domain_irq+0x64/0xb8 Feb 18 15:02:21 rou2 kernel: gic_handle_irq+0x50/0xa0 Feb 18 15:02:21 rou2 kernel: el1_irq+0xb8/0x180 Feb 18 15:02:21 rou2 kernel: arch_cpu_idle+0x10/0x18 Feb 18 15:02:21 rou2 kernel: do_idle+0x204/0x290 Feb 18 15:02:21 rou2 kernel: cpu_startup_entry+0x24/0x28 Feb 18 15:02:21 rou2 kernel: rest_init+0xd4/0xe0 Feb 18 15:02:21 rou2 kernel: arch_call_rest_init+0xc/0x14 Feb 18 15:02:21 rou2 kernel: start_kernel+0x420/0x44c Feb 18 15:02:21 rou2 kernel: ---[ end trace da7d1f37f9aaa781 ]--- Feb 18 15:02:21 rou2 kernel: usb 1-1.1: USB disconnect, device number 4 Feb 18 15:02:21 rou2 kernel: Unable to handle kernel NULL pointer dereference at virtual address 0000000000000200 Feb 18 15:02:21 rou2 kernel: Mem abort info: Feb 18 15:02:21 rou2 kernel: ESR = 0x96000004 Feb 18 15:02:21 rou2 kernel: EC = 0x25: DABT (current EL), IL = 32 bits Feb 18 15:02:21 rou2 kernel: SET = 0, FnV = 0 Feb 18 15:02:21 rou2 kernel: EA = 0, S1PTW = 0 Feb 18 15:02:21 rou2 kernel: Data abort info: Feb 18 15:02:21 rou2 kernel: ISV = 0, ISS = 0x00000004 Feb 18 15:02:21 rou2 kernel: CM = 0, WnR = 0 Feb 18 15:02:21 rou2 kernel: user pgtable: 4k pages, 48-bit VAs, pgdp=0000000042ad3000 Feb 18 15:02:21 rou2 kernel: [0000000000000200] pgd=0000000000000000 Feb 18 15:02:21 rou2 kernel: Internal error: Oops: 96000004 [#1] PREEMPT SMP Feb 18 15:02:21 rou2 kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 huawei_cdc_ncm cdc_wdm cdc_ncm option usbnet usb_wwan usbserial cpufreq_powersave cpufreq_conservative nf_log_ipv4 nf_log_common nft_limit xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core meson_gxbb_wdt scpi_hwmon ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 18 15:02:21 rou2 kernel: CPU: 0 PID: 2544 Comm: kworker/0:0 Tainted: G W 5.4.13-meson64 #20.02.2 Feb 18 15:02:21 rou2 kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 18 15:02:21 rou2 kernel: Workqueue: usb_hub_wq hub_event Feb 18 15:02:21 rou2 kernel: pstate: 40000005 (nZcv daif -PAN -UAO) Feb 18 15:02:21 rou2 kernel: pc : skb_release_data+0x84/0x178 Feb 18 15:02:21 rou2 kernel: lr : skb_release_all+0x24/0x30 Feb 18 15:02:21 rou2 kernel: sp : ffff800010003d20 Feb 18 15:02:21 rou2 kernel: x29: ffff800010003d20 x28: ffff00007eec63c0 Feb 18 15:02:21 rou2 kernel: x27: ffff8000113be6c0 x26: ffff8000113e18c8 Feb 18 15:02:21 rou2 kernel: cpufreq: __target_index: Failed to change cpu frequency: -5 Feb 18 15:02:21 rou2 kernel: x25: 0000000000000060 x24: 0000000000000002 -
Hello, I am using up to date Armbian Buster. TP-Link TL-WN722N V1 USB WiFi dongle causes system crashes after kernel upgrade to 5.4.12-meson64 #19.11.8 SMP PREEMPT Thu Jan 16 20:12:23 CET 2020 aarch64 GNU/Linux. Before updating the kernel, I had no such problem. Feb 12 20:17:15 xxx systemd[1]: Found device AR9271 802.11n. Feb 12 20:17:15 xxx systemd[1]: Started ifup for wlx54e6fc8d208e. Feb 12 20:17:15 xxx wpa_supplicant[2360]: Successfully initialized wpa_supplicant Feb 12 20:17:15 xxx sh[2344]: wlx54e6fc8d208e=wlx54e6fc8d208e Feb 12 20:17:17 xxx wpa_supplicant[2361]: Using interface wlx54e6fc8d208e with hwaddr 54:e6:fc:8d:20:8e and ssid "mynetwork" Feb 12 20:17:17 xxx wpa_supplicant[2361]: wlx54e6fc8d208e: interface state UNINITIALIZED->ENABLED Feb 12 20:17:17 xxx wpa_supplicant[2361]: wlx54e6fc8d208e: AP-ENABLED Feb 12 20:17:17 xxx wpa_supplicant[2361]: wlx54e6fc8d208e: CTRL-EVENT-CONNECTED - Connection to 54:e6:fc:8d:20:8e completed [id=0 id_str=] Feb 12 20:17:20 xxx systemd[1]: systemd-rfkill.service: Succeeded. Feb 12 20:17:41 xxx wpa_supplicant[2361]: wlx54e6fc8d208e: AP-STA-CONNECTED 2c:d0:5a:38:bd:3b Feb 12 20:18:00 xxx sshd[2403]: Accepted password for myuser from 10.0.0.5 port 22 ssh2 Feb 12 20:18:00 xxx sshd[2403]: pam_unix(sshd:session): session opened for user myuser by (uid=0) Feb 12 20:18:00 xxx systemd[1]: Created slice User Slice of UID 1001. Feb 12 20:18:00 xxx systemd[1]: Starting User Runtime Directory /run/user/1001... Feb 12 20:18:00 xxx systemd-logind[1584]: New session 7 of user myuser. Feb 12 20:18:00 xxx systemd[1]: Started User Runtime Directory /run/user/1001. Feb 12 20:18:00 xxx systemd[1]: Starting User Manager for UID 1001... Feb 12 20:18:00 xxx systemd[2406]: pam_unix(systemd-user:session): session opened for user myuser by (uid=0) Feb 12 20:18:00 xxx systemd[2406]: Reached target Paths. Feb 12 20:18:00 xxx systemd[2406]: Reached target Sockets. Feb 12 20:18:00 xxx systemd[2406]: Reached target Timers. Feb 12 20:18:00 xxx systemd[2406]: Reached target Basic System. Feb 12 20:18:00 xxx systemd[2406]: Reached target Default. Feb 12 20:18:00 xxx systemd[2406]: Startup finished in 123ms. Feb 12 20:18:00 xxx systemd[1]: Started User Manager for UID 1001. Feb 12 20:18:00 xxx systemd[1]: Started Session 7 of user myuser. Feb 12 20:18:48 xxx sshd[2505]: Received disconnect from 10.0.0.5 port 22:11: disconnected by user Feb 12 20:18:48 xxx sshd[2505]: Disconnected from user myuser 10.0.0.5 port 22 Feb 12 20:18:48 xxx sshd[2403]: pam_unix(sshd:session): session closed for user myuser Feb 12 20:18:48 xxx systemd[1]: session-7.scope: Succeeded. Feb 12 20:18:48 xxx systemd-logind[1584]: Session 7 logged out. Waiting for processes to exit. Feb 12 20:18:48 xxx systemd-logind[1584]: Removed session 7. Feb 12 20:18:54 xxx wpa_supplicant[2361]: wlx54e6fc8d208e: AP-STA-DISCONNECTED 2c:d0:5a:38:bd:3b Feb 12 20:18:56 xxx kernel: ath: phy0: Unable to remove station entry for: 2c:d0:5a:38:bd:3b Message from syslogd@localhost at Feb 12 20:18:59 ... kernel:[ 571.404886] Internal error: Oops: 96000004 [#1] PREEMPT SMP Message from syslogd@localhost at Feb 12 20:18:59 ... kernel:[ 571.612865] Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Message from syslogd@localhost at Feb 12 20:18:59 ... kernel:[ 571.623551] Kernel panic - not syncing: Attempted to kill init! exitcode=0x0000000b Second one: Feb 12 20:23:08 xxx wpa_supplicant[2125]: Using interface wlx54e6fc8d208e with hwaddr 54:e6:fc:8d:20:8e and ssid "mynetwork" Feb 12 20:23:08 xxx wpa_supplicant[2125]: wlx54e6fc8d208e: interface state UNINITIALIZED->ENABLED Feb 12 20:23:08 xxx wpa_supplicant[2125]: wlx54e6fc8d208e: AP-ENABLED Feb 12 20:23:08 xxx wpa_supplicant[2125]: wlx54e6fc8d208e: CTRL-EVENT-CONNECTED - Connection to 54:e6:fc:8d:20:8e completed [id=0 id_str=] Feb 12 20:23:11 xxx systemd[1]: systemd-rfkill.service: Succeeded. Message from syslogd@localhost at Feb 12 20:23:25 ... kernel:[ 77.921372] Internal error: Oops: 96000004 [#1] PREEMPT SMP Message from syslogd@localhost at Feb 12 20:23:25 ... kernel:[ 78.152254] Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:25 xxx kernel: Unable to handle kernel paging request at virtual address 0005001700000048 Feb 12 20:23:25 xxx kernel: Mem abort info: Feb 12 20:23:25 xxx kernel: ESR = 0x96000004 Feb 12 20:23:25 xxx kernel: EC = 0x25: DABT (current EL), IL = 32 bits Feb 12 20:23:25 xxx kernel: SET = 0, FnV = 0 Feb 12 20:23:25 xxx kernel: EA = 0, S1PTW = 0 Feb 12 20:23:25 xxx kernel: Data abort info: Feb 12 20:23:25 xxx kernel: ISV = 0, ISS = 0x00000004 Feb 12 20:23:25 xxx kernel: CM = 0, WnR = 0 Feb 12 20:23:25 xxx kernel: [0005001700000048] address between user and kernel address ranges Feb 12 20:23:25 xxx kernel: Internal error: Oops: 96000004 [#1] PREEMPT SMP Feb 12 20:23:25 xxx kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 cdc_ether usbnet uas nf_log_ipv4 nf_log_common nft_limit cpufreq_powersave cpufreq_conservative xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core meson_gxbb_wdt scpi_hwmon ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 12 20:23:25 xxx kernel: CPU: 1 PID: 2125 Comm: wpa_supplicant Not tainted 5.4.12-meson64 #19.11.8 Feb 12 20:23:25 xxx kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 12 20:23:25 xxx kernel: pstate: 60000005 (nZCv daif -PAN -UAO) Feb 12 20:23:25 xxx kernel: pc : __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:25 xxx kernel: lr : __kmalloc_node_track_caller+0x4c/0x288 Feb 12 20:23:25 xxx kernel: sp : ffff800010603710 Feb 12 20:23:25 xxx kernel: x29: ffff800010603710 x28: 0000000000000014 Feb 12 20:23:25 xxx kernel: x27: ffff80001249d3c0 x26: ffff000042d90d00 Feb 12 20:23:25 xxx kernel: x25: 00000000ffffffff x24: 0000000000159801 Feb 12 20:23:25 xxx kernel: x23: ffff800011c67510 x22: 00000000ffffffff Feb 12 20:23:25 xxx kernel: x21: 00000000000928c0 x20: 0005001700000048 Feb 12 20:23:25 xxx kernel: x19: ffff000007303800 x18: 0000000000000000 Feb 12 20:23:25 xxx kernel: x17: 0000000000000000 x16: 0000000000000000 Feb 12 20:23:25 xxx kernel: x15: 0000000000000000 x14: 85a901e7583f6960 Feb 12 20:23:25 xxx kernel: x13: 3c82001b6c5b05ca x12: 32d0f6c2e6c1b305 Feb 12 20:23:25 xxx kernel: x11: ed25b09923fa1d1c x10: 32b5a2a8b0fc50fa Feb 12 20:23:25 xxx kernel: x9 : 0000000000000000 x8 : ffff00003c5a1020 Feb 12 20:23:25 xxx kernel: x7 : 0000000000000000 x6 : ffff00003c5a1020 Feb 12 20:23:25 xxx kernel: x5 : 0000000000000020 x4 : 0000000000000000 Feb 12 20:23:25 xxx kernel: x3 : 0000000000159801 x2 : 0000000000000000 Feb 12 20:23:25 xxx kernel: x1 : ffff00003c56aac0 x0 : 0000000000000001 Feb 12 20:23:25 xxx kernel: Call trace: Feb 12 20:23:25 xxx kernel: __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:25 xxx kernel: __kmalloc_reserve.isra.56+0x44/0xa0 Feb 12 20:23:25 xxx kernel: pskb_expand_head+0x70/0x2d0 Feb 12 20:23:25 xxx kernel: netlink_trim+0xa0/0xe0 Feb 12 20:23:25 xxx kernel: netlink_unicast+0x54/0x1f8 Feb 12 20:23:25 xxx kernel: nl80211_tx_mgmt+0x32c/0x370 [cfg80211] Feb 12 20:23:25 xxx kernel: genl_family_rcv_msg+0x1dc/0x3b0 Feb 12 20:23:25 xxx kernel: genl_rcv_msg+0x58/0xd0 Feb 12 20:23:25 xxx kernel: netlink_rcv_skb+0x58/0x118 Feb 12 20:23:25 xxx kernel: genl_rcv+0x34/0x48 Feb 12 20:23:25 xxx kernel: netlink_unicast+0x180/0x1f8 Feb 12 20:23:25 xxx kernel: netlink_sendmsg+0x198/0x338 Feb 12 20:23:25 xxx kernel: sock_sendmsg+0x44/0x50 Feb 12 20:23:25 xxx kernel: ____sys_sendmsg+0x250/0x290 Feb 12 20:23:25 xxx kernel: ___sys_sendmsg+0x80/0xc0 Feb 12 20:23:25 xxx kernel: __sys_sendmsg+0x68/0xb8 Feb 12 20:23:25 xxx kernel: __arm64_sys_sendmsg+0x20/0x28 Feb 12 20:23:25 xxx kernel: el0_svc_common.constprop.2+0x88/0x150 Feb 12 20:23:25 xxx kernel: el0_svc_handler+0x20/0x80 Feb 12 20:23:25 xxx kernel: el0_svc+0x8/0xc Feb 12 20:23:25 xxx kernel: Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:25 xxx kernel: ---[ end trace 7b6592514db85574 ]--- Message from syslogd@localhost at Feb 12 20:23:26 ... kernel:[ 78.799696] Internal error: Oops: 96000004 [#2] PREEMPT SMP Message from syslogd@localhost at Feb 12 20:23:26 ... kernel:[ 79.010560] Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:26 xxx kernel: Unable to handle kernel paging request at virtual address 0005001700000048 Feb 12 20:23:26 xxx kernel: Mem abort info: Feb 12 20:23:26 xxx kernel: ESR = 0x96000004 Feb 12 20:23:26 xxx kernel: EC = 0x25: DABT (current EL), IL = 32 bits Feb 12 20:23:26 xxx kernel: SET = 0, FnV = 0 Feb 12 20:23:26 xxx kernel: EA = 0, S1PTW = 0 Feb 12 20:23:26 xxx kernel: Data abort info: Feb 12 20:23:26 xxx kernel: ISV = 0, ISS = 0x00000004 Feb 12 20:23:26 xxx kernel: CM = 0, WnR = 0 Feb 12 20:23:26 xxx kernel: [0005001700000048] address between user and kernel address ranges Feb 12 20:23:26 xxx kernel: Internal error: Oops: 96000004 [#2] PREEMPT SMP Feb 12 20:23:26 xxx kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 cdc_ether usbnet uas nf_log_ipv4 nf_log_common nft_limit cpufreq_powersave cpufreq_conservative xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core meson_gxbb_wdt scpi_hwmon ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 12 20:23:26 xxx kernel: CPU: 1 PID: 7 Comm: kworker/u8:0 Tainted: G D 5.4.12-meson64 #19.11.8 Feb 12 20:23:26 xxx kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 12 20:23:26 xxx kernel: Workqueue: phy0 ath9k_led_work [ath9k_htc] Feb 12 20:23:26 xxx kernel: pstate: 60000005 (nZCv daif -PAN -UAO) Feb 12 20:23:26 xxx kernel: pc : __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:26 xxx kernel: lr : __kmalloc_node_track_caller+0x4c/0x288 Feb 12 20:23:26 xxx kernel: sp : ffff80001005bbe0 Feb 12 20:23:26 xxx kernel: x29: ffff80001005bbe0 x28: 0000000000000000 Feb 12 20:23:26 xxx kernel: x27: ffff00000735a0b8 x26: ffff80001005bd70 Feb 12 20:23:26 xxx kernel: x25: 00000000ffffffff x24: 0000000000159801 Feb 12 20:23:26 xxx kernel: x23: ffff800011c62c54 x22: 00000000ffffffff Feb 12 20:23:26 xxx kernel: x21: 0000000000082a20 x20: 0005001700000048 Feb 12 20:23:26 xxx kernel: x19: ffff000007303800 x18: 0000000000000010 Feb 12 20:23:26 xxx kernel: x17: 0000000000000000 x16: 0000000000000000 Feb 12 20:23:26 xxx kernel: x15: 0000000000000000 x14: 3239353662372065 Feb 12 20:23:26 xxx kernel: x13: 0000000000000000 x12: 0000000000000001 Feb 12 20:23:26 xxx kernel: x11: 0000000000000000 x10: 00000000000009f0 Feb 12 20:23:26 xxx kernel: x9 : ffff80001005bd60 x8 : fefefefefefefeff Feb 12 20:23:26 xxx kernel: x7 : 0000000000000001 x6 : 0000000000000064 Feb 12 20:23:26 xxx kernel: x5 : 000000000000000c x4 : 0000000000000000 Feb 12 20:23:26 xxx kernel: x3 : 0000000000159801 x2 : 0000000000000000 Feb 12 20:23:26 xxx kernel: x1 : ffff000007395580 x0 : 0000000000000001 Feb 12 20:23:26 xxx kernel: Call trace: Feb 12 20:23:26 xxx kernel: __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:26 xxx kernel: __kmalloc_reserve.isra.56+0x44/0xa0 Feb 12 20:23:26 xxx kernel: __alloc_skb+0x84/0x198 Feb 12 20:23:26 xxx kernel: ath9k_wmi_cmd+0x6c/0x1c8 [ath9k_htc] Feb 12 20:23:26 xxx kernel: ath9k_reg_rmw+0x7c/0x170 [ath9k_htc] Feb 12 20:23:26 xxx kernel: ath9k_hw_set_gpio+0xa8/0xf0 [ath9k_hw] Feb 12 20:23:26 xxx kernel: ath9k_led_work+0x28/0x30 [ath9k_htc] Feb 12 20:23:26 xxx kernel: process_one_work+0x1e0/0x338 Feb 12 20:23:26 xxx kernel: worker_thread+0x40/0x440 Feb 12 20:23:26 xxx kernel: kthread+0x120/0x128 Feb 12 20:23:26 xxx kernel: ret_from_fork+0x10/0x18 Feb 12 20:23:26 xxx kernel: Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:26 xxx kernel: ---[ end trace 7b6592514db85575 ]--- Message from syslogd@localhost at Feb 12 20:23:47 ... kernel:[ 99.419758] Internal error: Oops: 96000004 [#3] PREEMPT SMP Message from syslogd@localhost at Feb 12 20:23:47 ... kernel:[ 99.642872] Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:46 xxx kernel: Unable to handle kernel paging request at virtual address 0005001700000048 Feb 12 20:23:46 xxx kernel: Mem abort info: Feb 12 20:23:46 xxx kernel: ESR = 0x96000004 Feb 12 20:23:46 xxx kernel: EC = 0x25: DABT (current EL), IL = 32 bits Feb 12 20:23:46 xxx kernel: SET = 0, FnV = 0 Feb 12 20:23:46 xxx kernel: EA = 0, S1PTW = 0 Feb 12 20:23:46 xxx kernel: Data abort info: Feb 12 20:23:46 xxx kernel: ISV = 0, ISS = 0x00000004 Feb 12 20:23:46 xxx kernel: CM = 0, WnR = 0 Feb 12 20:23:46 xxx kernel: [0005001700000048] address between user and kernel address ranges Feb 12 20:23:47 xxx kernel: Internal error: Oops: 96000004 [#3] PREEMPT SMP Feb 12 20:23:47 xxx kernel: Modules linked in: ath9k_htc ath9k_common ath9k_hw mac80211 ath cfg80211 rfkill libarc4 cdc_ether usbnet uas nf_log_ipv4 nf_log_common nft_limit cpufreq_powersave cpufreq_conservative xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat xt_MASQUERADE nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core meson_gxbb_wdt scpi_hwmon ip_tables x_tables dwmac_generic realtek dwmac_meson8b Feb 12 20:23:47 xxx kernel: CPU: 1 PID: 1557 Comm: systemd-timesyn Tainted: G D 5.4.12-meson64 #19.11.8 Feb 12 20:23:47 xxx kernel: Hardware name: Hardkernel ODROID-C2 (DT) Feb 12 20:23:47 xxx kernel: pstate: 60000005 (nZCv daif -PAN -UAO) Feb 12 20:23:47 xxx kernel: pc : __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:47 xxx kernel: lr : __kmalloc_node_track_caller+0x4c/0x288 Feb 12 20:23:47 xxx kernel: sp : ffff8000105f37c0 Feb 12 20:23:47 xxx kernel: x29: ffff8000105f37c0 x28: 0000000000000000 Feb 12 20:23:47 xxx kernel: x27: 0000000000000cc0 x26: 0000000000000000 Feb 12 20:23:47 xxx kernel: x25: 00000000ffffffff x24: 0000000000159801 Feb 12 20:23:47 xxx kernel: x23: ffff800011c62c54 x22: 00000000ffffffff Feb 12 20:23:47 xxx kernel: x21: 0000000000082cc0 x20: 0005001700000048 Feb 12 20:23:47 xxx kernel: x19: ffff000007303800 x18: 0000000000000000 Feb 12 20:23:47 xxx kernel: x17: 0000000000000000 x16: 0000000000000000 Feb 12 20:23:47 xxx kernel: x15: 0000000000000000 x14: 0000000000000000 Feb 12 20:23:47 xxx kernel: x13: 0000000000000001 x12: 0000000000000000 Feb 12 20:23:47 xxx kernel: x11: 0000000000000000 x10: 0000000000000000 Feb 12 20:23:47 xxx kernel: x9 : 0000000000000000 x8 : 00000000000005c8 Feb 12 20:23:47 xxx kernel: x7 : 0000000000000014 x6 : 0000000000000000 Feb 12 20:23:47 xxx kernel: x5 : ffff000042d90e00 x4 : ffff00007fbb42f0 Feb 12 20:23:47 xxx kernel: x3 : 0000000000159801 x2 : 0000000000000000 Feb 12 20:23:47 xxx kernel: x1 : ffff00007ef4e3c0 x0 : 0000000000000001 Feb 12 20:23:47 xxx kernel: Call trace: Feb 12 20:23:47 xxx kernel: __kmalloc_node_track_caller+0x150/0x288 Feb 12 20:23:47 xxx kernel: __kmalloc_reserve.isra.56+0x44/0xa0 Feb 12 20:23:47 xxx kernel: __alloc_skb+0x84/0x198 Feb 12 20:23:47 xxx kernel: alloc_skb_with_frags+0x50/0x1e0 Feb 12 20:23:47 xxx kernel: sock_alloc_send_pskb+0x200/0x238 Feb 12 20:23:47 xxx kernel: sock_alloc_send_skb+0x1c/0x28 Feb 12 20:23:47 xxx kernel: __ip_append_data.isra.59+0x770/0xc10 Feb 12 20:23:47 xxx kernel: ip_make_skb+0xe8/0x140 Feb 12 20:23:47 xxx kernel: udp_sendmsg+0x794/0xa10 Feb 12 20:23:47 xxx kernel: inet_sendmsg+0x40/0x68 Feb 12 20:23:47 xxx kernel: sock_sendmsg+0x44/0x50 Feb 12 20:23:47 xxx kernel: __sys_sendto+0xcc/0x130 Feb 12 20:23:47 xxx kernel: __arm64_sys_sendto+0x24/0x30 Feb 12 20:23:47 xxx kernel: el0_svc_common.constprop.2+0x88/0x150 Feb 12 20:23:47 xxx kernel: el0_svc_handler+0x20/0x80 Feb 12 20:23:47 xxx kernel: el0_svc+0x8/0xc Feb 12 20:23:47 xxx kernel: Code: d5384101 b9402262 b9401020 11000400 (f8626a99) Feb 12 20:23:47 xxx kernel: ---[ end trace 7b6592514db85576 ]---
-
Hello, After upgrade Armbian (4.19.69-meson64) to Armbian Buster with Linux 5.3.11-meson64 warning messages shows up on boot in dmesg: ... [ 1.973932] Key type encrypted registered [ 1.985109] dwc2 c9000000.usb: c9000000.usb supply vusb_d not found, using dummy regulator [ 1.985153] dwc2 c9000000.usb: c9000000.usb supply vusb_a not found, using dummy regulator [ 1.986616] phy phy-c0000000.phy.0: USB ID detect failed! [ 1.986623] phy phy-c0000000.phy.0: phy poweron failed --> -22 [ 1.986643] ------------[ cut here ]------------ [ 1.986700] WARNING: CPU: 3 PID: 68 at drivers/regulator/core.c:2036 _regulator_put+0x34/0xd8 [ 1.986702] Modules linked in: [ 1.986709] CPU: 3 PID: 68 Comm: kworker/3:1 Not tainted 5.3.11-meson64 #19.11.3 [ 1.986711] Hardware name: Hardkernel ODROID-C2 (DT) [ 1.986719] Workqueue: events deferred_probe_work_func [ 1.986724] pstate: 60000005 (nZCv daif -PAN -UAO) [ 1.986728] pc : _regulator_put+0x34/0xd8 [ 1.986732] lr : _regulator_put+0x34/0xd8 [ 1.986733] sp : ffff000011683af0 [ 1.986735] x29: ffff000011683af0 x28: 0000000000000000 [ 1.986739] x27: ffff80007f2ac6b8 x26: ffff000011106530 [ 1.986743] x25: 0000000000000000 x24: 0000000000000009 [ 1.986746] x23: ffff000011683bb8 x22: ffff80006a1c2b00 [ 1.986750] x21: ffff0000113916c8 x20: ffff80006a1c2d00 [ 1.986753] x19: ffff80006a1c2d00 x18: ffff0000113ae000 [ 1.986756] x17: 000000003ae42590 x16: 00000000ed672116 [ 1.986760] x15: 00000000fffffff0 x14: ffff0000114be0fa [ 1.986763] x13: 0000000000000000 x12: ffff0000114bd000 [ 1.986767] x11: ffff0000113ae000 x10: ffff0000114bd748 [ 1.986770] x9 : 0000000000000000 x8 : 0000000000000001 [ 1.986774] x7 : 00000000000000eb x6 : ffff0000114bd000 [ 1.986777] x5 : 0000000000000000 x4 : 0000000000000000 [ 1.986780] x3 : 00000000ffffffff x2 : 3c797d94ab3f0f00 [ 1.986783] x1 : 0000000000000000 x0 : 0000000000000024 [ 1.986787] Call trace: [ 1.986792] _regulator_put+0x34/0xd8 [ 1.986796] regulator_put+0x2c/0x40 [ 1.986800] regulator_bulk_free+0x30/0x50 [ 1.986805] devm_regulator_bulk_release+0x18/0x20 [ 1.986810] release_nodes+0x1b0/0x220 [ 1.986814] devres_release_all+0x34/0x58 [ 1.986818] really_probe+0x1b8/0x3d0 [ 1.986822] driver_probe_device+0xdc/0x130 [ 1.986825] __device_attach_driver+0x88/0x108 [ 1.986828] bus_for_each_drv+0x78/0xc8 [ 1.986831] __device_attach+0xd4/0x158 [ 1.986834] device_initial_probe+0x10/0x18 [ 1.986837] bus_probe_device+0x90/0x98 [ 1.986840] deferred_probe_work_func+0x88/0xd8 [ 1.986846] process_one_work+0x1e0/0x338 [ 1.986850] worker_thread+0x240/0x440 [ 1.986854] kthread+0x120/0x128 [ 1.986859] ret_from_fork+0x10/0x18 [ 1.986861] ---[ end trace 629d4ecc13425951 ]--- [ 1.986907] ------------[ cut here ]------------ [ 1.986942] WARNING: CPU: 3 PID: 68 at drivers/regulator/core.c:2036 _regulator_put+0x34/0xd8 [ 1.986943] Modules linked in: [ 1.986948] CPU: 3 PID: 68 Comm: kworker/3:1 Tainted: G W 5.3.11-meson64 #19.11.3 [ 1.986950] Hardware name: Hardkernel ODROID-C2 (DT) [ 1.986954] Workqueue: events deferred_probe_work_func [ 1.986958] pstate: 60000005 (nZCv daif -PAN -UAO) [ 1.986962] pc : _regulator_put+0x34/0xd8 [ 1.986965] lr : _regulator_put+0x34/0xd8 [ 1.986967] sp : ffff000011683af0 [ 1.986969] x29: ffff000011683af0 x28: 0000000000000000 [ 1.986972] x27: ffff80007f2ac6b8 x26: ffff000011106530 [ 1.986976] x25: 0000000000000000 x24: 0000000000000009 [ 1.986979] x23: ffff000011683bb8 x22: ffff80006a1c2b00 [ 1.986983] x21: ffff0000113916c8 x20: ffff80006a1c2e00 [ 1.986986] x19: ffff80006a1c2e00 x18: ffff0000113ae000 [ 1.986989] x17: 000000003ae42590 x16: 00000000ed672116 [ 1.986993] x15: 00000000fffffff0 x14: ffff0000114be0fa [ 1.986996] x13: 0000000000000000 x12: ffff0000114bd000 [ 1.987000] x11: ffff0000113ae000 x10: ffff0000114bd748 [ 1.987003] x9 : 0000000000000000 x8 : 0000000000000001 [ 1.987006] x7 : 0000000000000118 x6 : ffff0000114bd000 [ 1.987010] x5 : 0000000000000000 x4 : 0000000000000000 [ 1.987013] x3 : 00000000ffffffff x2 : 3c797d94ab3f0f00 [ 1.987016] x1 : 0000000000000000 x0 : 0000000000000024 [ 1.987019] Call trace: [ 1.987023] _regulator_put+0x34/0xd8 [ 1.987027] regulator_put+0x2c/0x40 [ 1.987030] regulator_bulk_free+0x30/0x50 [ 1.987034] devm_regulator_bulk_release+0x18/0x20 [ 1.987038] release_nodes+0x1b0/0x220 [ 1.987041] devres_release_all+0x34/0x58 [ 1.987044] really_probe+0x1b8/0x3d0 [ 1.987048] driver_probe_device+0xdc/0x130 [ 1.987051] __device_attach_driver+0x88/0x108 [ 1.987053] bus_for_each_drv+0x78/0xc8 [ 1.987056] __device_attach+0xd4/0x158 [ 1.987059] device_initial_probe+0x10/0x18 [ 1.987062] bus_probe_device+0x90/0x98 [ 1.987065] deferred_probe_work_func+0x88/0xd8 [ 1.987069] process_one_work+0x1e0/0x338 [ 1.987072] worker_thread+0x240/0x440 [ 1.987075] kthread+0x120/0x128 [ 1.987078] ret_from_fork+0x10/0x18 [ 1.987081] ---[ end trace 629d4ecc13425952 ]--- [ 1.987135] dwc2: probe of c9000000.usb failed with error -22 [ 1.987536] dwc2 c9100000.usb: c9100000.usb supply vusb_d not found, using dummy regulator [ 1.987581] dwc2 c9100000.usb: c9100000.usb supply vusb_a not found, using dummy regulator [ 2.024002] mmc0: new HS200 MMC card at address 0001 ... I haven't had any system hangups yet but I am worried.
-

[Odroid C2] Ethernet interface meson8b-dwmac lockup on medium traffic
zanzibar replied to zanzibar's topic in Amlogic meson
Issue fixed with Armbian (19.11.3) and kernel upgrade to 5.3.11. -
Hello, I am using up to date Armbian - Debian Buster with Armbian Linux 4.19.69-meson64 Linux version 4.19.69-meson64 (root@builder) (gcc version 7.4.1 20181213 [linaro-7.4-2019.02 revision 56ec6f6b99cc167ff0c2f8e1a2eed33b1edc85d4] (Linaro GCC 7.4-2019.02)) #5.95 SMP PREEMPT Mon Sep 2 01:21:39 CEST 2019. I have encountered Ethernet interface lockup on medium traffic (after 30s-120s when copying big files from external usb disk by sshfs - 240Mb/s). At high/medium Ethernet traffic the issue always occurs. It is most likely caused by some kernel update because I didn't have such problem before. Similar issue: https://github.com/rockchip-linux/kernel/issues/27 [ 1584.165514] EXT4-fs (sda1): mounted filesystem with ordered data mode. Opts: discard [ 1689.827553] ------------[ cut here ]------------ [ 1689.827600] NETDEV WATCHDOG: eth0 (meson8b-dwmac): transmit queue 0 timed out [ 1689.827721] WARNING: CPU: 0 PID: 0 at net/sched/sch_generic.c:461 dev_watchdog+0x2b4/0x2c0 [ 1689.827736] Modules linked in: uas nf_log_ipv4 nf_log_common nft_limit xt_tcpudp xt_multiport xt_LOG xt_limit xt_conntrack nft_counter nft_chain_nat_ipv4 ipt_MASQUERADE nf_nat_ipv4 nf_nat nf_conntrack nf_defrag_ipv6 nf_defrag_ipv4 nft_compat nf_tables nfnetlink meson_rng rng_core scpi_hwmon meson_gxbb_wdt ip_tables x_tables realtek [ 1689.827866] CPU: 0 PID: 0 Comm: swapper/0 Not tainted 4.19.69-meson64 #5.95 [ 1689.827871] Hardware name: Hardkernel ODROID-C2 (DT) [ 1689.827881] pstate: 20000005 (nzCv daif -PAN -UAO) [ 1689.827892] pc : dev_watchdog+0x2b4/0x2c0 [ 1689.827901] lr : dev_watchdog+0x2b4/0x2c0 [ 1689.827906] sp : ffff000008003da0 [ 1689.827912] x29: ffff000008003da0 x28: 0000000000000005 [ 1689.827926] x27: 0000000000000020 x26: 00000000ffffffff [ 1689.827939] x25: 0000000000000140 x24: ffff800071250480 [ 1689.827952] x23: ffff80007125045c x22: ffff800070ca5940 [ 1689.827965] x21: ffff000008e77000 x20: ffff800071250000 [ 1689.827978] x19: 0000000000000000 x18: ffffffffffffffff [ 1689.827991] x17: 0000000000000000 x16: 0000000000000000 [ 1689.828004] x15: ffff000008e93000 x14: 00000000fffffff0 [ 1689.828017] x13: ffff000008f2786a x12: ffff000008e93000 [ 1689.828030] x11: 0000000000000000 x10: ffff000008f26000 [ 1689.828043] x9 : 0000000000000000 x8 : 0000000000000001 [ 1689.828055] x7 : 0000000000000000 x6 : 0000000000000123 [ 1689.828068] x5 : 0000000000000000 x4 : 0000000000000001 [ 1689.828080] x3 : 0000000000000000 x2 : ffff000008e7c358 [ 1689.828093] x1 : 2481295eb9750900 x0 : 0000000000000000 [ 1689.828105] Call trace: [ 1689.828117] dev_watchdog+0x2b4/0x2c0 [ 1689.828131] call_timer_fn+0x20/0x78 [ 1689.828143] expire_timers+0xa4/0xb0 [ 1689.828154] run_timer_softirq+0xe4/0x1a0 [ 1689.828164] __do_softirq+0x10c/0x200 [ 1689.828174] irq_exit+0xac/0xc0 [ 1689.828186] __handle_domain_irq+0x60/0xb0 [ 1689.828194] gic_handle_irq+0x58/0xa8 [ 1689.828201] el1_irq+0xb0/0x128 [ 1689.828212] arch_cpu_idle+0x10/0x18 [ 1689.828220] do_idle+0x1d4/0x298 [ 1689.828229] cpu_startup_entry+0x20/0x28 [ 1689.828243] rest_init+0xcc/0xd8 [ 1689.828256] start_kernel+0x3d4/0x400 [ 1689.828269] ---[ end trace b79bbf67547ae10f ]--- [ 1689.828334] meson8b-dwmac c9410000.ethernet eth0: Reset adapter. [ 1689.909766] RTL8211F Gigabit Ethernet stmmac-0:00: attached PHY driver [RTL8211F Gigabit Ethernet] (mii_bus:phy_addr=stmmac-0:00, irq=37) [ 1689.922902] meson8b-dwmac c9410000.ethernet eth0: No Safety Features support found [ 1689.922925] meson8b-dwmac c9410000.ethernet eth0: PTP not supported by HW [ 1693.046757] meson8b-dwmac c9410000.ethernet eth0: Link is Up - 1Gbps/Full - flow control rx/tx [ 1737.955616] meson8b-dwmac c9410000.ethernet eth0: Reset adapter. [ 1738.037764] RTL8211F Gigabit Ethernet stmmac-0:00: attached PHY driver [RTL8211F Gigabit Ethernet] (mii_bus:phy_addr=stmmac-0:00, irq=37) [ 1738.050715] meson8b-dwmac c9410000.ethernet eth0: No Safety Features support found [ 1738.050737] meson8b-dwmac c9410000.ethernet eth0: PTP not supported by HW [ 1741.822114] meson8b-dwmac c9410000.ethernet eth0: Link is Up - 1Gbps/Full - flow control rx/tx
-
Hello, Recently I have discovered bug in kernel or maybe iptables with using Huawei E3372h LTE Hi-Link USB dongle (or maybe other devices which exposes HTTP interfaces over cdc_ether). Odroid enters into kernel panic and reboot. I am using ARMBIAN 5.85 stable Debian GNU/Linux 9 (stretch) 4.19.42-meson64. kernel:[ 60.801868] Internal error: Oops: 96000004 [#1] PREEMPT SMP The steps to recreate the bug: 1) disable or remove NetworkManager, use only IPv4, 2) set network interfaces in /etc/network/interfaces source /etc/network/interfaces.d/* auto lo iface lo inet loopback auto eth0 allow-hotplug eth0 iface eth0 inet static address 10.0.0.1 netmask 255.255.255.0 allow-hotplug enxXXX iface enxXXX inet dhcp enxXXX - is example name of your E3372h (virtual?) ethernet interface. 3) check settings in /etc/sysctl.conf - you need have some routing capabilites on - mine is: kernel.printk = 3 4 1 3 net.ipv4.conf.default.rp_filter=1 net.ipv4.conf.all.rp_filter=1 net.ipv4.tcp_syncookies=1 net.ipv4.ip_forward=1 net.ipv4.conf.all.accept_redirects = 0 net.ipv6.conf.all.accept_redirects = 0 net.ipv4.conf.all.secure_redirects = 0 net.ipv4.conf.all.send_redirects = 0 net.ipv4.conf.all.accept_source_route = 0 net.ipv6.conf.all.accept_source_route = 0 net.ipv6.conf.all.disable_ipv6=1 net.ipv4.icmp_echo_ignore_broadcasts=1 net.ipv4.icmp_echo_ignore_all=1 vm.swappiness=100 4) set iptables rules to forward packets between local eth0 and usb dongle ethernet: *nat :PREROUTING ACCEPT [0:0] :INPUT ACCEPT [0:0] :OUTPUT ACCEPT [0:0] :POSTROUTING ACCEPT [0:0] -A POSTROUTING -o enxXXX -j MASQUERADE COMMIT *filter :INPUT DROP [0:0] :FORWARD DROP [0:0] :OUTPUT DROP [0:0] :interfaces - [0:0] :open - [0:0] -A INPUT -m conntrack --ctstate ESTABLISHED -j ACCEPT -A INPUT -j interfaces -A INPUT -j open -A INPUT -j DROP -A FORWARD -i enxXXX -o eth0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT -A FORWARD -i eth0 -o enxXXX -p tcp -m multiport --dports 80,443,9001,9111,3690 -j ACCEPT -A FORWARD -i eth0 -o enxXXX -p icmp -m icmp --icmp-type 8 -j ACCEPT -A FORWARD -j DROP -A OUTPUT -j ACCEPT -A interfaces -i lo -j ACCEPT COMMIT 5) connect to local eth0 other computer (set static IP to eg. 10.0.0.2, netmask 255.255.255.0 and gateway 10.0.0.1), 6) from other computer you should be able to ping E3372h eth interface: 192.168.8.1, 7) open web browser (I have Firefox) - enter address: http://192.168.8.1 8) after 5-10 seconds kernel panic occurs 9) after reboot there is a green background on screen via HDMI (need to hard power off and on to start without green screen). I have attached two fotos: 1 - kernel oops messages; 2 - green screen. Has anyone had a similar problem?
-
Hello, I using up to date Armbian Stretch with kernel 4.19.41-meson64 #5.85 SMP PREEMPT Wed May 8 12:40:37 CEST 2019 aarch64 GNU/Linux. Today about 2 minutes after system boot I have found this warning in kernel log: May 12 07:51:48 xxx kernel: WARNING: CPU: 1 PID: 0 at kernel/time/hrtimer.c:917 hrtimer_forward+0x88/0xd0 May 12 07:51:48 xxx kernel: Modules linked in: cdc_ether usbnet uas xt_tcpudp nf_log_ipv4 nf_log_common xt_LOG xt_multiport xt_conntrack iptable_filter ipt_MASQUERADE iptable_nat nf_nat_ipv4 nf_nat nf_connt May 12 07:51:48 xxx kernel: CPU: 1 PID: 0 Comm: swapper/1 Not tainted 4.19.41-meson64 #5.85 May 12 07:51:48 xxx kernel: Hardware name: Hardkernel ODROID-C2 (DT) May 12 07:51:48 xxx kernel: pstate: 20000085 (nzCv daIf -PAN -UAO) May 12 07:51:48 xxx kernel: pc : hrtimer_forward+0x88/0xd0 May 12 07:51:48 xxx kernel: lr : txdone_hrtimer+0xd0/0x108 May 12 07:51:48 xxx kernel: sp : ffff00000800be20 May 12 07:51:48 xxx kernel: x29: ffff00000800be20 x28: ffff80007ff8a580 May 12 07:51:48 xxx kernel: x27: ffff00000891a6d8 x26: 0000000000000001 May 12 07:51:48 xxx kernel: x25: 0000000000000000 x24: 0000000000000001 May 12 07:51:48 xxx kernel: x23: ffff8000710c4be8 x22: 00000000000000f8 May 12 07:51:48 xxx kernel: x21: ffff8000710c4bb8 x20: ffff8000710c4ac0 May 12 07:51:48 xxx kernel: x19: 00000000000f4240 x18: 0000000000000000 May 12 07:51:48 xxx kernel: x17: 0000000000000000 x16: 0000000000000000 May 12 07:51:48 xxx kernel: x15: 000000000000029a x14: 0000000000000400 May 12 07:51:48 xxx kernel: x13: 0000000000000001 x12: 0000000000000001 May 12 07:51:48 xxx kernel: x11: 0000000000ad3d80 x10: 0000000000000040 May 12 07:51:48 xxx kernel: x9 : ffff000008e93418 x8 : ffff800071400248 May 12 07:51:48 xxx kernel: x7 : ffff800071400288 x6 : 00000000d138f0b4 May 12 07:51:48 xxx kernel: x5 : 0000000000000001 x4 : ffff8000710c4be8 May 12 07:51:48 xxx kernel: x3 : 0000002116b3f554 x2 : 00000000000f4240 May 12 07:51:48 xxx kernel: x1 : 0000002116b3f76a x0 : 0000000000000216 May 12 07:51:48 xxx kernel: Call trace: May 12 07:51:48 xxx kernel: hrtimer_forward+0x88/0xd0 May 12 07:51:48 xxx kernel: __hrtimer_run_queues+0x120/0x1b8 May 12 07:51:48 xxx kernel: hrtimer_interrupt+0xd4/0x250 May 12 07:51:48 xxx kernel: arch_timer_handler_phys+0x28/0x40 May 12 07:51:48 xxx kernel: handle_percpu_devid_irq+0x80/0x138 May 12 07:51:48 xxx kernel: generic_handle_irq+0x24/0x38 May 12 07:51:48 xxx kernel: __handle_domain_irq+0x5c/0xb0 May 12 07:51:48 xxx kernel: gic_handle_irq+0x58/0xa8 May 12 07:51:48 xxx kernel: el1_irq+0xb0/0x128 May 12 07:51:48 xxx kernel: arch_cpu_idle+0x10/0x18 May 12 07:51:48 xxx kernel: do_idle+0x1d4/0x298 May 12 07:51:48 xxx kernel: cpu_startup_entry+0x20/0x28 May 12 07:51:48 xxx kernel: secondary_start_kernel+0x194/0x1d0 May 12 07:51:48 xxx kernel: ---[ end trace dcd1d1f08e0ad792 ]--- When it happened I had one USB device connected to ODROID - E3372h LTE modem (and it was online). But system working normally after that. I've never had such warning before (with previous kernel - 4.19.20). Maybe it has something to do with the last Armbian kernel update?
-

[ODROID C2] USB Wifi dongle TL-WN722N - system crash and reboot
zanzibar replied to zanzibar's topic in Amlogic meson
This happened only once. I can't reproduce this bug since then. I have seen that raspberry had similar problems(long time ago): https://www.raspberrypi.org/forums/viewtopic.php?t=49840 -
Hello, I using up to date Armbian Stretch with kernel 4.19.41-meson64 #5.85 SMP PREEMPT Wed May 8 12:40:37 CEST 2019 aarch64 GNU/Linux. I started using TP-Link TL-WN722N V1 USB WiFi dongle recently. Unfortunately Armbian has crashed and rebooted once during I using such USB dongle. I tried to reproduce this bug once more but I can't. I have installed firmware-atheros package for this USB dongle. Should I install armbian-firmware-full package instead of firmware-atheros? It could help? Log:
-
@TonyMac32 Thanks armbianmonitor -U http://ix.io/1DAM
-
@TonyMac32 I have exacly this module (orange): https://www.hardkernel.com/shop/16gb-emmc-module-c2-linux Reference chart (including performance tests): https://wiki.odroid.com/accessory/emmc/reference_chart Here is my dmesg about eMMC: [ 2.759256] mmc0: new HS200 MMC card at address 0001 [ 2.760146] mmcblk0: mmc0:0001 AJTD4R 14.6 GiB [ 2.760815] mmcblk0boot0: mmc0:0001 AJTD4R partition 1 4.00 MiB [ 2.761489] mmcblk0boot1: mmc0:0001 AJTD4R partition 2 4.00 MiB [ 2.761603] mmcblk0rpmb: mmc0:0001 AJTD4R partition 3 4.00 MiB, chardev (244:0) [ 2.762360] mmcblk0: p1 Extcsd data: root@odroidc2:~# mmc extcsd read /dev/mmcblk0 ============================================= Extended CSD rev 1.8 (MMC 5.1) ============================================= Card Supported Command sets [S_CMD_SET: 0x01] HPI Features [HPI_FEATURE: 0x01]: implementation based on CMD13 Background operations support [BKOPS_SUPPORT: 0x01] Max Packet Read Cmd [MAX_PACKED_READS: 0x3f] Max Packet Write Cmd [MAX_PACKED_WRITES: 0x3f] Data TAG support [DATA_TAG_SUPPORT: 0x01] Data TAG Unit Size [TAG_UNIT_SIZE: 0x02] Tag Resources Size [TAG_RES_SIZE: 0x00] Context Management Capabilities [CONTEXT_CAPABILITIES: 0x05] Large Unit Size [LARGE_UNIT_SIZE_M1: 0x07] Extended partition attribute support [EXT_SUPPORT: 0x03] Generic CMD6 Timer [GENERIC_CMD6_TIME: 0x0a] Power off notification [POWER_OFF_LONG_TIME: 0x3c] Cache Size [CACHE_SIZE] is 65536 KiB Background operations status [BKOPS_STATUS: 0x00] 1st Initialisation Time after programmed sector [INI_TIMEOUT_AP: 0x1e] Power class for 52MHz, DDR at 3.6V [PWR_CL_DDR_52_360: 0x00] Power class for 52MHz, DDR at 1.95V [PWR_CL_DDR_52_195: 0x00] Power class for 200MHz at 3.6V [PWR_CL_200_360: 0x00] Power class for 200MHz, at 1.95V [PWR_CL_200_195: 0x00] Minimum Performance for 8bit at 52MHz in DDR mode: [MIN_PERF_DDR_W_8_52: 0x00] [MIN_PERF_DDR_R_8_52: 0x00] TRIM Multiplier [TRIM_MULT: 0x02] Secure Feature support [SEC_FEATURE_SUPPORT: 0x55] Boot Information [BOOT_INFO: 0x07] Device supports alternative boot method Device supports dual data rate during boot Device supports high speed timing during boot Boot partition size [BOOT_SIZE_MULTI: 0x20] Access size [ACC_SIZE: 0x07] High-capacity erase unit size [HC_ERASE_GRP_SIZE: 0x01] i.e. 512 KiB High-capacity erase timeout [ERASE_TIMEOUT_MULT: 0x01] Reliable write sector count [REL_WR_SEC_C: 0x01] High-capacity W protect group size [HC_WP_GRP_SIZE: 0x10] i.e. 8192 KiB Sleep current (VCC) [S_C_VCC: 0x07] Sleep current (VCCQ) [S_C_VCCQ: 0x07] Sleep/awake timeout [S_A_TIMEOUT: 0x11] Sector Count [SEC_COUNT: 0x01d1f000] Device is block-addressed Minimum Write Performance for 8bit: [MIN_PERF_W_8_52: 0x00] [MIN_PERF_R_8_52: 0x00] [MIN_PERF_W_8_26_4_52: 0x00] [MIN_PERF_R_8_26_4_52: 0x00] Minimum Write Performance for 4bit: [MIN_PERF_W_4_26: 0x00] [MIN_PERF_R_4_26: 0x00] Power classes registers: [PWR_CL_26_360: 0x00] [PWR_CL_52_360: 0x00] [PWR_CL_26_195: 0x00] [PWR_CL_52_195: 0x00] Partition switching timing [PARTITION_SWITCH_TIME: 0x02] Out-of-interrupt busy timing [OUT_OF_INTERRUPT_TIME: 0x0a] I/O Driver Strength [DRIVER_STRENGTH: 0x1f] Card Type [CARD_TYPE: 0x57] HS200 Single Data Rate eMMC @200MHz 1.8VI/O HS Dual Data Rate eMMC @52MHz 1.8V or 3VI/O HS eMMC @52MHz - at rated device voltage(s) HS eMMC @26MHz - at rated device voltage(s) CSD structure version [CSD_STRUCTURE: 0x02] Command set [CMD_SET: 0x00] Command set revision [CMD_SET_REV: 0x00] Power class [POWER_CLASS: 0x00] High-speed interface timing [HS_TIMING: 0x02] Erased memory content [ERASED_MEM_CONT: 0x00] Boot configuration bytes [PARTITION_CONFIG: 0x48] Boot Partition 1 enabled No access to boot partition Boot config protection [BOOT_CONFIG_PROT: 0x00] Boot bus Conditions [BOOT_BUS_CONDITIONS: 0x01] High-density erase group definition [ERASE_GROUP_DEF: 0x01] Boot write protection status registers [BOOT_WP_STATUS]: 0x00 Boot Area Write protection [BOOT_WP]: 0x00 Power ro locking: possible Permanent ro locking: possible ro lock status: not locked User area write protection register [USER_WP]: 0x00 FW configuration [FW_CONFIG]: 0x00 RPMB Size [RPMB_SIZE_MULT]: 0x20 Write reliability setting register [WR_REL_SET]: 0x1f user area: the device protects existing data if a power failure occurs during a write operation partition 1: the device protects existing data if a power failure occurs during a write operation partition 2: the device protects existing data if a power failure occurs during a write operation partition 3: the device protects existing data if a power failure occurs during a write operation partition 4: the device protects existing data if a power failure occurs during a write operation Write reliability parameter register [WR_REL_PARAM]: 0x14 Device supports the enhanced def. of reliable write Enable background operations handshake [BKOPS_EN]: 0x00 H/W reset function [RST_N_FUNCTION]: 0x01 HPI management [HPI_MGMT]: 0x01 Partitioning Support [PARTITIONING_SUPPORT]: 0x07 Device support partitioning feature Device can have enhanced tech. Max Enhanced Area Size [MAX_ENH_SIZE_MULT]: 0x0003a3 i.e. 7626752 KiB Partitions attribute [PARTITIONS_ATTRIBUTE]: 0x00 Partitioning Setting [PARTITION_SETTING_COMPLETED]: 0x00 Device partition setting NOT complete General Purpose Partition Size [GP_SIZE_MULT_4]: 0x000000 [GP_SIZE_MULT_3]: 0x000000 [GP_SIZE_MULT_2]: 0x000000 [GP_SIZE_MULT_1]: 0x000000 Enhanced User Data Area Size [ENH_SIZE_MULT]: 0x000000 i.e. 0 KiB Enhanced User Data Start Address [ENH_START_ADDR]: 0x000000 i.e. 0 bytes offset Bad Block Management mode [SEC_BAD_BLK_MGMNT]: 0x00 Periodic Wake-up [PERIODIC_WAKEUP]: 0x00 Program CID/CSD in DDR mode support [PROGRAM_CID_CSD_DDR_SUPPORT]: 0x01 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[127]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[126]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[125]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[124]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[123]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[122]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[121]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[120]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[119]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[118]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[117]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[116]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[115]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[114]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[113]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[112]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[111]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[110]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[109]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[108]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[107]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[106]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[105]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[104]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[103]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[102]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[101]]: 0x05 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[100]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[99]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[98]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[97]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[96]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[95]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[94]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[93]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[92]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[91]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[90]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[89]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[88]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[87]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[86]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[85]]: 0x01 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[84]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[83]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[82]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[81]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[80]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[79]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[78]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[77]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[76]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[75]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[74]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[73]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[72]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[71]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[70]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[69]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[68]]: 0xc8 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[67]]: 0xc8 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[66]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[65]]: 0x00 Vendor Specific Fields [VENDOR_SPECIFIC_FIELD[64]]: 0x0f Native sector size [NATIVE_SECTOR_SIZE]: 0x00 Sector size emulation [USE_NATIVE_SECTOR]: 0x00 Sector size [DATA_SECTOR_SIZE]: 0x00 1st initialization after disabling sector size emulation [INI_TIMEOUT_EMU]: 0x00 Class 6 commands control [CLASS_6_CTRL]: 0x00 Number of addressed group to be Released[DYNCAP_NEEDED]: 0x00 Exception events control [EXCEPTION_EVENTS_CTRL]: 0x0000 Exception events status[EXCEPTION_EVENTS_STATUS]: 0x0000 Extended Partitions Attribute [EXT_PARTITIONS_ATTRIBUTE]: 0x0000 Context configuration [CONTEXT_CONF[51]]: 0x00 Context configuration [CONTEXT_CONF[50]]: 0x00 Context configuration [CONTEXT_CONF[49]]: 0x00 Context configuration [CONTEXT_CONF[48]]: 0x00 Context configuration [CONTEXT_CONF[47]]: 0x00 Context configuration [CONTEXT_CONF[46]]: 0x00 Context configuration [CONTEXT_CONF[45]]: 0x00 Context configuration [CONTEXT_CONF[44]]: 0x00 Context configuration [CONTEXT_CONF[43]]: 0x00 Context configuration [CONTEXT_CONF[42]]: 0x00 Context configuration [CONTEXT_CONF[41]]: 0x00 Context configuration [CONTEXT_CONF[40]]: 0x00 Context configuration [CONTEXT_CONF[39]]: 0x00 Context configuration [CONTEXT_CONF[38]]: 0x00 Context configuration [CONTEXT_CONF[37]]: 0x00 Packed command status [PACKED_COMMAND_STATUS]: 0x00 Packed command failure index [PACKED_FAILURE_INDEX]: 0x00 Power Off Notification [POWER_OFF_NOTIFICATION]: 0x01 Control to turn the Cache ON/OFF [CACHE_CTRL]: 0x01 eMMC Firmware Version: Command Queue Support [CMDQ_SUPPORT]: 0x01 Command Queue Depth [CMDQ_DEPTH]: 16 Command Enabled [CMDQ_MODE_EN]: 0x00 @Strykar So You have also too small read speeds on Armbian: https://wiki.odroid.com/accessory/emmc/reference_chart ("ODROID-C2 + Black eMMC Performance Test of File I/O").
-
Hello, I have 16GB orange eMMC v0.4 module for Odroid C2. I have installed on it Armbian Debian Stretch Next (mainline kernel). When I run iozone I got read results that is slower than eMMC Hardkernel specs. root@odroidc2:~# iozone -e -I -a -s 100M -r 4k -r 16k -r 512k -r 1024k -r 16384k -i 0 -i 1 -i 2 Iozone: Performance Test of File I/O Version $Revision: 3.429 $ Compiled for 64 bit mode. Build: linux Contributors:William Norcott, Don Capps, Isom Crawford, Kirby Collins Al Slater, Scott Rhine, Mike Wisner, Ken Goss Steve Landherr, Brad Smith, Mark Kelly, Dr. Alain CYR, Randy Dunlap, Mark Montague, Dan Million, Gavin Brebner, Jean-Marc Zucconi, Jeff Blomberg, Benny Halevy, Dave Boone, Erik Habbinga, Kris Strecker, Walter Wong, Joshua Root, Fabrice Bacchella, Zhenghua Xue, Qin Li, Darren Sawyer, Vangel Bojaxhi, Ben England, Vikentsi Lapa. Run began: Sun Feb 10 03:49:18 2019 Include fsync in write timing O_DIRECT feature enabled Auto Mode File size set to 102400 kB Record Size 4 kB Record Size 16 kB Record Size 512 kB Record Size 1024 kB Record Size 16384 kB Command line used: iozone -e -I -a -s 100M -r 4k -r 16k -r 512k -r 1024k -r 16384k -i 0 -i 1 -i 2 Output is in kBytes/sec Time Resolution = 0.000001 seconds. Processor cache size set to 1024 kBytes. Processor cache line size set to 32 bytes. File stride size set to 17 * record size. random random bkwd record stride kB reclen write rewrite read reread read write read rewrite read fwrite frewrite fread freread 102400 4 32953 36184 23772 23774 23679 25934 102400 16 39075 44064 42145 42258 41967 43945 102400 512 40897 41149 80160 80028 79930 41461 102400 1024 41512 41928 82305 82300 82167 42205 102400 16384 41108 43502 86202 86228 86214 43877 On Hardkernel Ubuntu when I run iozone I have max ~50 MB/s write and ~133MB/s read, but on Armbian only max ~86 MB/s read. Why is that?
-

[ODROID C2] USB ports are (still?) not working properly
zanzibar replied to zanzibar's topic in Amlogic meson
I found easy workaround. Add usbcore.autosuspend=-1 as kernel parameter by /boot/armbianEnv.txt file. Eg.: extraargs=usbcore.autosuspend=-1 Of course this workaround have cons: odroid c2 will take more power. @TonyMac32 Could you please give me more details where I should look for this issue in source files? Is it dwc2 usb driver? -
Hello, I have installed Armbian Debian Stretch Next (mainline kernel) on my Odroid C2 and updated to newest version(apt update & apt upgrade). Everything works fine except USB ports. I have USB LTE modem which is not recognized. I have tried "lsusb -v" but with this modem not works. But when I connect USB keyboard first then "lsusb -v" and next I connect LTE modem and type "lsusb -v" then it's works. I also tried connecting USB LTE modem before Odroid C2 boot but this workaround not working. Is there any workaround which not involving connecting more than one USB device? Maybe usb kernel modules (usbcore, ehci_hcd, ...) compiled as external modules will help find workaround?