Search the Community
Showing results for tags 'tutorial'.
-
Hello, I apologize in advance if I haven't put the topic in the right section. I want to share my experience with NanoPC-T6 and two NVMe m.2 disk. I use my NanoPC-T6 for a small server. In the beginning I had 2 SSDs and an M.2 to 2 SATA adapter. But I never found the right solution to power both the NanoPC-T6 and the SSDs from 1 place. After some internet searching I was able to find a solution on how to put 2 NVMe drives on my NanoPC-T6 As you know NanoPC-T6 has 1 M.2 M-Key connector with PCIe 3.0 x4 There is also one PCIe which is M.2 E-key connector with PCIe 2.1 x1 With this adapter: https://www.aliexpress.com/item/1005004762924052.html I am using M.2 E-key to M.2 M-Key. The version of the kernel I use is 6.1.43-vendor-rk35xx. The speed that the NVMe disk on the adapter board can reach is about 400MB per second, which is quite good for my needs. I am attaching some pictures. I hope this is useful for you. If there are any questions, I'm at the meeting to answer them. Regards,
-
Step 1 - Install the Armbian PGP key and update your APT sources Install armbian.gpg to /usr/share/keyrings/armbian.gpg (mode 644) You can use a copy from another one of your SBCs, or... ... you can download and install like below (thanks @BrewNinja for the example) touch /usr/share/keyrings/armbian.gpg chmod 644 /usr/share/keyrings/armbian.gpg wget https://apt.armbian.com/armbian.key -O - | gpg --dearmor >/usr/share/keyrings/armbian.gpg Edit /etc/apt/sources.list Replace all instances of bullseye with bookworm Edit /etc/apt/sources.list.d/armbian.list deb [signed-by=/usr/share/keyrings/armbian.gpg] http://apt.armbian.com bookworm main bookworm-utils bookworm-desktop Edit any other files in /etc/apt/sources.list.d as appropriate, to replace bullseye with bookworm Step 2 apt update Step 3 NOTE - WHEN RUNNING THE BELOW COMMANDS, DO NOT ACCEPT ANY INTERACTIVE PROMPTS FOR CHANGING /etc/initramfs-tools/initramfs.conf The default is not to accept the changes anyway - but I am noting this here to be extra careful I've checked - the changes may differ from what armbian has in the latest images apt upgrade --no-new-pkgs apt full-upgrade apt dist-upgrade
-
Sharing is caring. Did finally manage to get this working. So lets make it simple clever. Actually i did this on a 64bit raspian light kernel 6.1 but it must be the same on Armbian 10 jan 24 Sharing the Raspberry Pi's WiFi over the ethernet port sudo apt get update && sudo apt install dnsmasq iptables iptables-persistent dhcpcd5 sudo vim /etc/dhcpcd.conf interface eth0 static ip_address=192.168.4.1/24 ------- sudo mv /etc/dnsmasq.conf /etc/dnsmasq.conf.bk sudo nano /etc/dnsmasq.conf - interface=eth0 dhcp-range=192.168.4.8,192.168.4.250,255.255.255.0,12h server=8.8.8.8 bogus-priv ------ sudo systemctl restart dnsmasq.service ------ sudo vim /etc/sysctl.conf net.ipv4.ip_forward=1 ------- sudo systemctl start dnsmasq ------- sudo sh -c "echo 1 > /proc/sys/net/ipv4/ip_forward" ------- sudo iptables -t nat -A POSTROUTING -o wlan0 -j MASQUERADE sudo iptables -A FORWARD -i wlan0 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT sudo iptables -A FORWARD -i eth0 -o wlan0 -j ACCEPT ------- sudo iptables -L -n -v ---------- sudo sh -c "iptables-save > /etc/iptables.ipv4.nat" --------- sudo vim /etc/rc.local iptables-restore < /etc/iptables.ipv4.nat exit0 --------- sudo reboot -------- Did get a perfect internet connection on odroid n2+ through eth0 - so the rpi4b is now supplying wifi for that board and providing petitboot with netbooting images through netboot_default after exit to shell.
-
Hello, this quick tutorial is to introduce an experimental Debian and Ubuntu APT repository to install ffmpeg and mpv compiled with v4l2request and v4l2drmprime patches developed by Linux kernel, LIbreELEC and Kodi folks to allow hardware video decoding on stateless decoders like those implemented in Rockchip and Allwinner SoCs for h.264, h.265, vp8 and vp9 codecs. The repository introduces a new package ffmpeg-v4l2request that integrates and substitues the base ffmpeg package and its related packages. Also provides mpv 0.35.1 for Ubuntu Jammy, which has an overrall better support for hardware video decoders. Preconditions: Kernel should be 6.1 or more recent armhf or arm64 architecture Supported operating systems are Debian Bookworm and Ubuntu Jammy Rockchip and Allwinner have already been tested, but this should work on other platforms with stateless decoders supported in kernel APT REPOSITORY SETUP To install the repository, just copy and paste the lines for your operating system in a terminal For Debian Bookworm: $ sudo wget http://apt.undo.it:7241/apt.undo.it.asc -O /etc/apt/trusted.gpg.d/apt.undo.it.asc $ echo "deb http://apt.undo.it:7241/debian bookworm main" | sudo tee /etc/apt/sources.list.d/apt.undo.it.list For Ubuntu Jammy: $ sudo wget http://apt.undo.it:7241/apt.undo.it.asc -O /etc/apt/trusted.gpg.d/apt.undo.it.asc $ echo "deb http://apt.undo.it:7241/ubuntu jammy main" | sudo tee /etc/apt/sources.list.d/apt.undo.it.list INSTALL FFMPEG AND MPV PACKAGES $ sudo apt update $ sudo apt install ffmpeg-v4l2request mpv SETUP MPV CONFIG FILE $ sudo mkdir -p /etc/mpv $ echo -e "hwdec=drm\ndrm-drmprime-video-plane=primary\ndrm-draw-plane=overlay" | sudo tee /etc/mpv/mpv.conf You can now play your videos using mpv and they should run with hardware decoding if supported, either in virtual terminals or in X11/Wayland windows! Enjoy! Notes: your mileage may vary a lot: the more recent is the kernel version, the better is support (you may need edge kernel) bug: when rendered in X11/Wayland window, video may show scattered tiles during frames bug: Lima driver (Mali 400/450) shows a red/pink tint when video is played in X11/Wayland (see https://github.com/mpv-player/mpv/issues/12968) (workaround below: https://forum.armbian.com/topic/32449-repository-for-v4l2request-hardware-video-decoding-rockchip-allwinner/?do=findComment&comment=177968) Panfrost driver should work flawlessy 10 bit HEVC are generally supported on all Rockchip devices (rk322x, rk3288, rk33x8, rk3399), but Allwinner H3 have no hardware support for that
-
Hi, after having a hard time getting the ILI9341 touchscreen working with the NanoPi Neo (Allwinner H3) it seems to work now. To have more GPIOs available for other stuff the touch and display need to share SPI0 I would like to upload it to github because there is basically nothing out of the box available but I'm a total noob with NanoPi, Armbian and overlays so maybe someone could look at it. root@nanopineo:~# uname -a Linux nanopineo 5.15.93-sunxi #23.02.2 SMP Fri Feb 17 00:00:00 UTC 2023 armv7l armv7l armv7l GNU/Linux This is the wiring between ILI9341 and NanoPi Neo: /* 3.3v <--> VCC & LED GND <--> GND PC2 <--> SCK & T_CLK PC1 <--> SDO<MISO> & T_DO PC0 <--> SDI<MOSI> & T_DIN PA1 <--> DC PG8 <--> RESET PC3 <--> CS PA3 <--> T_CS PG9 <--> T_IRG */ This is the overlay: /dts-v1/; /plugin/; / { compatible = "allwinner,sun8i-h3"; fragment@0 { target = <&pio>; __overlay__ { spi0_cs1: spi0_cs1 { pins = "PC3"; function = "gpio_out"; output-high; }; spi1_cs1: spi1_cs1 { pins = "PA3"; function = "gpio_out"; output-high; }; opiz_display_pins: opiz_display_pins { pins = "PA1", "PG8", "PA6"; function = "gpio_out"; }; ads7846_pins: ads7846_pins { pins = "PG9"; function = "irq"; }; }; }; fragment@1 { target = <&spi1>; __overlay__ { pinctrl-names = "default", "default"; pinctrl-1 = <&spi1_cs1>; cs-gpios = <0>, <&pio 0 3 0>; /* PA3 */ }; }; fragment@2 { target = <&spi0>; __overlay__ { #address-cells = <1>; #size-cells = <0>; status = "okay"; pinctrl-names = "default", "default"; cs-gpios= <&pio 2 3 0>, <&pio 0 3 1>; opizdisplay: opiz-display@0 { pinctrl-1 = <&spi0_cs1>; reg = <0>; /* Chip Select 0 */ compatible = "ilitek,ili9341"; spi-max-frequency = <1000000>; status = "okay"; pinctrl-names = "default"; pinctrl-0 = <&opiz_display_pins>; rotate = <90>; bgr = <0>; fps = <33>; buswidth = <8>; dc-gpios = <&pio 0 1 0>; /* PIN_22 GPIOA1 > */ reset-gpios = <&pio 6 8 1 >; /* GPIOG8> */ /*led-gpios=<&pio 0 6 0>; PIN_12 GPIOA6 > */ debug=<4>; }; ads7846: ads7846@1 { reg = <1>; /* Chip Select 1 */ compatible = "ti,ads7846"; spi-max-frequency = <1000000>; status = "okay"; pinctrl-2=<&spi1_cs1 &spi1_cs1>; pinctrl-names = "default"; pinctrl-3 = <&ads7846_pins>; interrupt-parent = <&pio>; interrupts = <6 9 2>; /* PG9 IRQ_TYPE_EDGE_FALLING */ pendown-gpio = <&pio 6 9 0>; /* PG9 */ /* driver defaults, optional */ ti,x-min = /bits/ 16 <0>; ti,y-min = /bits/ 16 <0>; ti,x-max = /bits/ 16 <0x0FFF>; ti,y-max = /bits/ 16 <0x0FFF>; ti,pressure-min = /bits/ 16 <0>; ti,pressure-max = /bits/ 16 <0xFFFF>; ti,x-plate-ohms = /bits/ 16 <400>; }; }; }; }; This is the /boot/armbianEnv.txt verbosity=1 bootlogo=false console=serial disp_mode=1920x1080p60 overlay_prefix=sun8i-h3 overlays=usbhost1 usbhost2 spi0 param_spidev_spi_bus=0 param_spidev_spi_cs=1 param_spidev_spi_cs=0 rootdev=UUID=XYZ-LONG-UUID-IS-LONG rootfstype=ext4 user_overlays=ili-touch-spi usbstoragequirks=0x2537:0x1066:u,0x2537:0x1068:u After connecting via ssh and starting evtest it shows this when touched ( not sure if it shows the correct coordinates yet ) Event: time 1682020476.763295, -------------- SYN_REPORT ------------ Event: time 1682020476.775286, type 3 (EV_ABS), code 0 (ABS_X), value 535 Event: time 1682020476.775286, type 3 (EV_ABS), code 1 (ABS_Y), value 3553 Event: time 1682020476.775286, type 3 (EV_ABS), code 24 (ABS_PRESSURE), value 65169 So it looks like everything is working but to be on the safe side I would like to wait until some pro reviewed the overlay. Thanks.
-
If you want to do a complete headless install of Armbian OS on an Orange Pi 5, and connect with Windows Remote Desktop, I put together what has worked for me. I pieced this tutorial together using an Orange Pi 5, installing Armbian 23.02 Jammy Gnome Desktop, and connecting via a Windows 11 PC using Windows Remote Desktop client. Keep in mind, your Orange Pi OS needs to be a full Desktop edition, otherwise, if you're using CLI editions, you will not have a Graphical User Interface installed, which Windows Remote Desktop needs to connect. ArmbianOS Download Link Putty Download Link Start PUTTY and enter your Orange Pi's IP address or host name (orangepi5) into PUTTY's Host Name field, hit enter. Accept any certificate popup screens. Login with Armbian's default user and pass. USER(logon): root PASSWORD: 1234 You'll be prompted with your Orange Pi's IP address. Take note of that, you might want to use it to remote connect, though you can also use the Orange Pi default hostname (orangepi5). Next, you'll be prompted to complete the following...create a root password, select bash or zsh, create a user and user password, enter real name, select timezone, and select locale. Take note of the User Name and Password you created since you will use that to logon with the Windows Remote Desktop Client. After completing account setup, you should be at a blank command prompt. DO NOT RUN ANY UPDATE COMMANDS enter the following commands... sudo apt install xrdp xorgxrdp sudo systemctl enable xrdp sudo systemctl status xrdp After entering the systemctl status xrdp command , you should see a listing showing "Active: active (running)". If Active shows "failed" then you will not be capable of connecting via Remote Desktop. **See below to try and resolve this issue. If you get a successful status list then, press the Ctrl key and C key simultaneously to get back to the command prompt. Reboot your Orange Pi by entering sudo reboot You should now be capable of accessing your OrangePi remotely by using Windows Remote Desktop. Open your Windows Remote Desktop client. You can adjust the size of the Remote Desktop screen session by clicking the "Show Options" located at the lower left corner of the Remote Desktop logon windows, then click the "Display" tab to set your preferred screen size, among other options. In the Computer field, enter your Orange Pi's IP address or host name (orangepi5), hit Connect. You should now be prompted with an XRDP logon screen. Enter the username and password you created when setting up Armbian during the PUTYY session. **INSTRUCTION TO ATTEMPT TO RESOLVE A FAILED SYSTEMCTL STATUS. If you haven't rebooted, and need to get back to the command prompt, then press the Ctrl key and C key simultaneously to get back to the command prompt. Enter the following commands to uninstall xrdp... sudo apt remove xrdp sudo apt purge xrdp Reinstall xrdp by following the same instructions at the start of this tutorial. Check the status again by entering the following command... sudo systemctl status xrdp Hopefully, this time it will show as "Active: active (running)". Hope this helps.
-
Hello im new and im Italian so i hope you will not hate me if i write not perfectly (Who said Google Translate?? No No No) This Guide is for a "client to client" setup of the box, we will internally switch Wifi to Eth, so a working computer can access internet from its eth port even if the router signal source is wireless. Router AP -----> ARM BOX [WIFI internal or usb dongle] ===>> internal eth0 ------> ethernet cable --> client eth port Make sure WiFi in arm box is connected using nmtui command FROM NOW ON <WIFI CARD> is the wifi adapter name es: replace "<WIFI CARD>" with "wlx0013eff301ee" Execute: sudo apt-get update && sudo apt-get install dnsmasq iptables iptables-persistent -y say no to save actual iptables rules (we dont have any yet) Edit /etc/network/interfaces comment if exist the part of eth0 "iface eth0" to "#iface eth0" add those lines allow-hotplug eth0 iface eth0 inet static address 172.24.1.1 netmask 255.255.255.0 network 172.24.1.0 broadcast 172.24.1.255 dns-nameservers 1.1.1.1 1.0.0.1 #########{Static}########### up ip addr add 172.24.0.1/24 dev eth0 execute those commands REMEMBER TO REPLACE <WIFI CARD> ip addr add 172.24.0.1/24 dev eth0 iptables -A FORWARD -o <WIFI CARD> -i eth0 -s 172.24.0.0/24 -m conntrack --ctstate NEW -j ACCEPT iptables -A FORWARD -m conntrack --ctstate ESTABLISHED,RELATED -j ACCEPT iptables -t nat -F POSTROUTING iptables -t nat -A POSTROUTING -o <WIFI CARD> -j MASQUERADE sh -c "iptables-save > /etc/iptables.ipv4.nat" sh -c "echo 1 > /proc/sys/net/ipv4/ip_forward" /etc/init.d/dnsmasq stop cp /etc/dnsmasq.conf /etc/dnsmasq.conf-backup Edit /etc/dnsmasq.conf inserting interface=eth0 listen-address=172.24.1.1 bind-interfaces server=1.1.1.1 domain-needed bogus-priv dhcp-range=172.24.0.100,172.24.0.250,72h Edit /etc/sysctl.conf inserting net.ipv4.conf.default.forwarding=1 net.ipv4.conf.all.forwarding=1 Edit /etc/rc.local inserting before "exit 0" iptables-restore < /etc/iptables.ipv4.nat execute those commands systemctl enable dnsmasq systemctl enable iptables Explainations: We set static net to eht0 then we set routing in iptables [forward and back] wlan<->eth then we make this setup persistent so that will persist after reboot. Working on my RK3318 Armbian bullseye 5.15 minimal and USB3 dongle RTL8814AU (also tested with a 8812au)
-
Hello Everyone This is my first topic here. To help myself in the future I did a guide to adjust armbian configuration and settings. This guide contains topics like: Maintaining the board updated Adjusting personal settings (keyboard, timezone, locale) Setting the sound output (default sound output to HDMI) Disable the desktop environment Setting the numlock to "ON" at start up Dealing with 4k video resolution It was based on my experience dealing with Orangepi PC (H3), but many things could be reused to others boards. I hope this guide may be helpful: https://github.com/lbmendes/armbian-settings/blob/main/README.md
-
!! DEPRECATED !! Instructions in this thread are oudated and superseded by the new experimental APT repository for hardware video decoding ffmpeg. Please refer to this thread from now on! Hello, recent upgrades to armbian are regarding kernel 5.15. I noticed that many v4l2 fixes and enhancements went into this release, so I decided to compile ffmpeg using LibreELEC patched version and mpv over it. mpv turns out to be statically linked with ffmpeg, so I propose it here for people who is interested in cutting edge kernel and wants to do some tests. This has been tested on Debian Bullseye and Ubuntu Hirsute on following platforms: Rockchip RK3228/9 (kernel 5.10, 5.14) Rockchip RK3288 (kernel 5.14) Rockchip RK3318/28 (kernel 5.15) It should work on allwinner platforms too, but I didn't test it there. Binaries are built by me on developing boards. The binary for armhf is available here The binary for arm64 is available here Copy the binary into /usr/local/bin directory of your system (mpv-armhf for 32 bit systems, mpv-arm64 for 64 bit systems): sudo cp mpv-armhf /usr/local/bin/mpv Install dependencies for Debian Bullseye and Ubuntu Hirsute: apt install libass9 libbluray2 librubberband2 libsdl2-2.0-0 libva-drm2 libva-wayland2 libva-x11-2 libva2 libvdpau1 libx264-160 libx265-192 libxss1 libxv1 libfdk-aac2 I have had issues with dependencies on Debian Buster/Ubuntu Focal, in particular libx264-160 and libx265-192 are not available there. I Solved the issue downloading the packages from Debian Bullseye web page and manually installing them. There may be the need for some other dependency depending upon your actual installation. Run mpv in a virtual terminal (videos up to 4K) with this CLI: mpv --vo=gpu --hwdec=drm --gpu-hwdec-interop=drmprime-drm --drm-draw-plane=overlay --drm-drmprime-video-plane=primary <video.mp4> Mpv can be run in X11 with this other CLI, but due to buffer copying it requires a good CPU - rk3228 and rk3328 won't even play 720p, rk3288 do 720p fine: mpv --vo=gpu --hwdec=auto-copy --gpu-context=x11egl --gpu-hwdec-interop=drmprime-drm <video.mp4> This is an experiment and your mileage may vary a lot: H.264 codec should be well supported around the boards; H.265 has more limited support VP8 should be generally supported VP9 seems to still require some work.
-
I have written a shell script that can make your Armbian installation run on a ZFS root. It has not been tested enough for my liking. Use at your own risk. Before running this script, please make a full backup of all your mission-critical files. URL: https://www.dropbox.com/s/ya3expllg1bqgfg/fructify.20211011.sh.gz To install the script, please run these commands:- # sudo wget https://www.dropbox.com/s/ya3expllg1bqgfg/fructify.20211011.sh.gz -O /usr/local/bin/fructify.sh.gz # sudo gunzip /usr/local/bin/fructify.sh.gz # sudo chmod +x /usr/local/bin/fructify.sh Oh, and install ZFS on your own OS installation. To use the script, either download an existing Armbian image or use your own system as the basis for the new installation. Next, please make sure (i) there is a blank micro-SD card in an adapter, (ii) the adapter is plugged into a USB port, and (iii) you know which /dev entry refers to that adapter’s USB port. It will probably be /dev/sda; please do not assume so. In the below commands, replace sdX with sda (or whatever). Method 1: Download and use an existing Armbian image # wget https://mirrors.netix.net/armbian/dl/nanopineo3/archive/Armbian_21.08.1_Nanopineo3_focal_current_5.10.60.img.xz -O /root/npneo3_focal.img.xz # xz -d /root/npneo3_focal.img.xz # fructify.sh /root/npneo3_focal.img.xz zfs /root/out.img # dd status=progress bs=1024k if=/root/out.img of=/dev/sdX Method 2: Use your existing filesystem as the basis # fructify.sh / zfs /dev/sdX In either case, please take care not to write the image to the wrong device. This script can also work with btrfs, ext4, or xfs. The script assumes that you have only one partition on your boot drive. That drive is usually /dev/mmcblk0; the boot/root partition is expected to be /dev/mmcblk0p1. It may be that the script also works if the boot drive is /dev/mmcblk1 and the boot/root partition is /dev/mmcblk1p1; I do not know. In any case, the script shrinks partition #1 (for boot) and allocates approximately 4GB to a newly created partition #2 (for root). If you create a ready-to-install Armbian image and boot it on a micro-SD card, the OS will expand partition #2 to fill the remainder of the micro-SD card. If you create a ZFS-ified (or whatever) copy of your existing installation, the SD card’s second partition will already have been expanded by the script itself. All feedback is welcome. I am new at this. Thank you.
-
Canon provides source code for cups driver, but with some proprietary binary libs. This libs available only for x86. No way for direct compiling cnijfilter for ARM (and other architectures). But we have qemu! We can transparently run x86 executables on any other host architectures. Easy steps to run cnijfilter on ARM (or any other arch): - Build https://github.com/endlessm/cnijfilter-common for x86 - Copy all needed x86 libs using recursive ldd. And copy it to /usr/lib/bjlib/ - Patch all executables: set interpreter to /usr/lib/bjlib/x86/ld-linux.so.2 and rpath to /usr/lib/bjlib/ - Install these patched packages to ARM system - Install qemu-user and qemu-user-binfmt (or qemu-arm-static) You do not need to do this manually. I have implemented an automated build system: https://github.com/Azq2/cnijfilter-arm-build All you need is any x86 machine to do the build. How to use 1. On any x86 machine: # Install dependencies sudo apt install debootstrap git util-linux # Get build system git clone https://github.com/Azq2/cnijfilter-arm-build # Start building cd cnijfilter-arm-build sudo ./build.sh build # Get .deb packages ls -lah ./result/full ls -lah ./result/light After build we have two variants of packages: full and light Item Full Light PPD files + + CUPS filters + + CUPS backends + - lgmon + - canon-maintenance + - cngpij + - cngpijmnt + - cnijlgmon2 + - cnijnetprn + - cnijnpr + - docs + - In most cases, a light package is completely sufficient: - We don't need canon usb backend, because cups have builtin USB support - We don't need canon network backend, because cups have builtin BJNP support (package cups-backend-bjnp) - Other canon maintenance utils are useless (in my opinion) 2. Copy .deb from result/light or result/full to your ARM machine. 3. On your ARM machine: # Install dependencies sudo apt install qemu-user qemu-user-binfmt # or sudo apt install qemu-user-static # Install common for all printers package sudo dpkg -i cnijfilter-common.deb # Install printer-specific package # Choose right package for your printer! e400series only for reference! sudo dpkg -i cnijfilter-e400series.deb 4. Done. You can now configure CUPS. Security with apparmor (optional) CUPS filters don't need any specific permissions. Create file /etc/apparmor.d/cnijfilter-filters with contents: #include <tunables/global> /usr/bin/bjfilter* { #include <abstractions/base> @{PROC}/sys/vm/mmap_min_addr r, } /usr/bin/cif[a-z]*[0-9d]* { #include <abstractions/base> @{PROC}/sys/vm/mmap_min_addr r, } /usr/lib/cups/filter/{cmdtocanonij,pstocanonbj,pstocanonij} { #include <abstractions/base> @{PROC}/sys/vm/mmap_min_addr r, } Then restart apparmor: sudo systemctl reload apparmor sudo aa-enforce cnijfilter-filters Note: this minimal file full coverage all executables in light package. For full package you need write additional rules by yourself.
-
Dear Armbian community, although I'm using Armbian a lot, I never had to submit anything to this forum (fortunately, because it works so well :-)), On my PC I've experienced lags on heavy IO operations. After a short dig into available information, I found a useful Cloudflare article on Kernel queues together with dm-crypt. A good & short summary on possible actions for users can be found here: https://wiki.archlinux.org/index.php/Dm-crypt/Specialties#Disable_workqueue_for_increased_solid_state_drive_(SSD)_performance Enabling the no-read-workqueue & no-write-workqueue options helped a lot! As I'm using a RockPi4 with the NVMe SSD with encryption, I thought this should apply to my SBC as well. Unfortunately, Armbian/Debian Buster uses cryptsetup v2.1.0 which does NOT support these options. According to the changelog, this option was introduced in v2.3.4: https://gitlab.com/cryptsetup/cryptsetup/-/blob/master/docs/v2.3.4-ReleaseNotes As Armbian uses a kernel > 5.9, the kernel infrastructure should be available. Fortunately, crypsetup v2.3.4 exists in the buster-backports repo: https://packages.debian.org/buster-backports/cryptsetup Solution: # sudo apt install cryptsetup/buster-backports
-
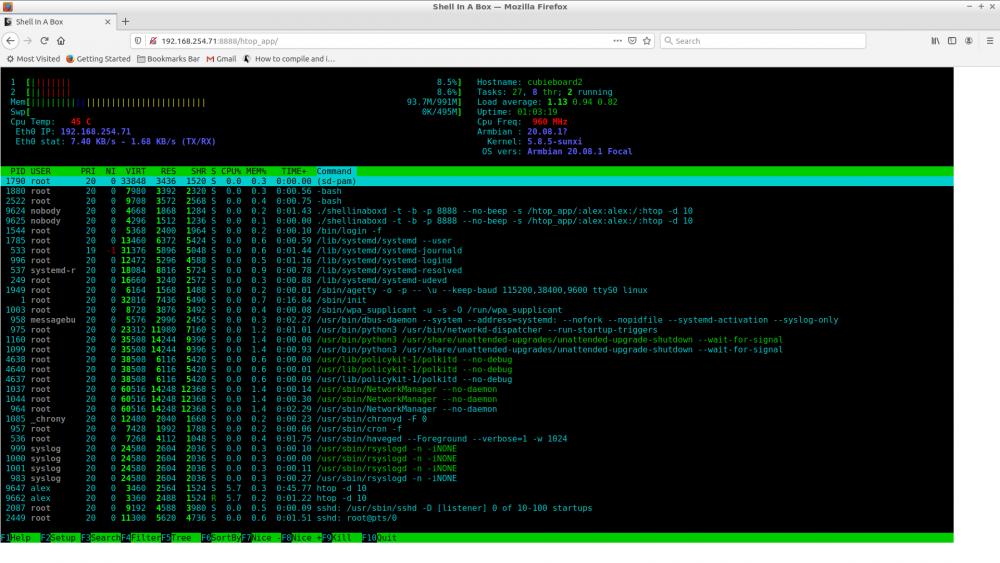
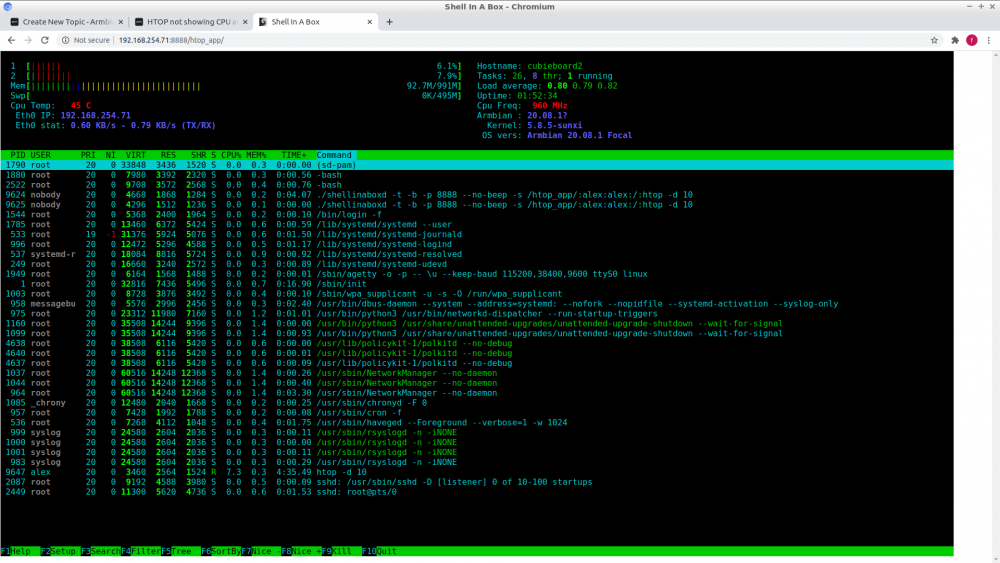
Here are the instructions to run Htop remotely using a web browser. I often use Htop to monitor the health of my boards and servers (amd64). It is a good tool for the sys admin to monitor the servers in real-time without much resources and it is not very intrusive. Recipe 1 - Clone shellinabox root@cubieboard2:~# git clone https://github.com/shellinabox/shellinabox Cloning into 'shellinabox'... remote: Enumerating objects: 3073, done. remote: Total 3073 (delta 0), reused 0 (delta 0), pack-reused 3073 Receiving objects: 100% (3073/3073), 4.31 MiB | 1.89 MiB/s, done. Resolving deltas: 100% (2418/2418), done. root@cubieboard2:~# cd shellinabox/ 2 - Build and install shellinabox shellinabox makefile is outdated for OpenSSL 1.1.y, so we need to bypass the linking process and do it manually. During the config process you get some errors, bypass the error by doing like so: root@cubieboard2:~/shellinabox# apt-get install libtool root@cubieboard2:~/shellinabox# autoreconf -i root@cubieboard2:~/shellinabox# autoconf root@cubieboard2:~/shellinabox# autoreconf -i root@cubieboard2:~/shellinabox# ./configure root@cubieboard2:~/shellinabox# make 3 - Bypass the linking error During the link process you get a missing openssl 1.1 lib, we then manually link shellinabox: root@cubieboard2:~/shellinabox# gcc -g -std=gnu99 -Wall -Os -o shellinaboxd shellinabox/shellinaboxd.o shellinabox/externalfile.o shellinabox/launcher.o shellinabox/privileges.o shellinabox/service.o shellinabox/session.o shellinabox/usercss.o ./.libs/liblogging.a ./.libs/libhttp.a -ldl -lutil -lssl -lcrypto 4 - Running Htop on the Browser I choose not to install shellinabox, just run a service to be able to run and make Htop available on the Browser. Tested on Google Chromium and FireFox (linux). root@cubieboard2:~/shellinabox# ./shellinaboxd -t -b -p 8888 --no-beep -s '/htop_app/:alex:alex:/:htop -d 10' where 8888 is the port. alex:alex is the user:group to run Htop with. Use yours [user] and [group]. Note: for security reason if you run with nobody:nogroup you wont be able to add or change any config on the Htop. Now fire the browser at http://ip_address:8888/htop_app/ and that's it, enjoy. 5 - Credits stackverflow, user ofstudio. Screenshot:
-
I got my hands on a "Set 9" Orange Pi Lite + GC2035 camera a while back and I've finally been able to put together a self-contained object detection device using Tensorflow, without sending any image data outside for processing. Basically, its a python Flask application that captures frames from the camera using a GStreamer pipeline. It runs them through a Tensorflow object detection model and spits out the same frame with extra metadata about objects it found, and renders a box around them. Using all four cores of the H2 it can do about 2-3 fps. The app keeps track of the count of all object types it has seen and exposes the metrics in prometheus format, for easy creation of graphs of what it sees over time with Grafana I'll explain some of the more interesting aspects of how I got this to work here in case anyone else wants to try to get some use out of this very inexpensive hardware, and I am grateful to the many posts on this forum that helped me along the way! Use a 3.4 kernel with custom GC2035 driver Don't bother with anything new - the GC2035 was hopeless on any newer builds of Armbian I tried. The driver available at https://github.com/avafinger/gc2035.git provided far better image quality. After installing the updated GC2035, I run the following to get the camera up and running: sudo sunxi-pio -m "PG11<1><0><1><1>" sudo modprobe gc2035 hres=1 sudo modprobe vfe_v4l2 Install Tensorflow lite runtime Google provides a tensorflow runtime as a binary wheel built for python 3.5 armv7. When pip installing, expect it to take 20 minutes or so as it will need to compile numpy (the apt repo version isn't recent enough) wget https://github.com/google-coral/pycoral/releases/download/release-frogfish/tflite_runtime-2.5.0-cp35-cp35m-linux_armv7l.whl sudo -H pip3 install tflite_runtime-2.5.0-cp35-cp35m-linux_armv7l.whl Build opencv for python 3.5 bindings This was something I tried everything I could to avoid, but I just could not get the colour conversion from the YUV format of the GC2035 to an RGB image using anything else I found online, so I was dependent on a single color-conversion utility function. To build the 3.4.12 version for use with python (grab lunch - takes about 1.5 hours :-O ) cmake -DCMAKE_INSTALL_PREFIX=/home/atomic/local -DSOFTFP=ON \ -DBUILD_TESTS=OFF -D BUILD_PERF_TESTS=OFF -D BUILD_opencv_python2=0 \ -D BUILD_opencv_python3=1 -D WITH_GSTREAMER=ON \ -D PYTHON3_INCLUDE_PATH=/usr/include/python3.5 .. make -j 4 make install # Check that ~/local/lib/python3.5/dist-packages should now have the cv2 shlib export PYTHONPATH=/home/atomic/local/lib/python3.5/dist-packages Build gstreamer plugin for Cedar H264 encoder This is required to get a working gstreamer pipeline for the video feed: git clone https://github.com/gtalusan/gst-plugin-cedar ./autogen.sh sudo make install # When trying against a pipc I had to copy into .local to get gstreamer to recognise it cp /usr/local/lib/gstreamer-1.0/libgst* ~/.local/share/gstreamer-1.0/plugins/ # Confirm that plugin is installed: gst-inspect-1.0 cedar_h264enc Processing images The full app source is on github, but the more interesting parts that took me some time to figure out were about getting python to cooperate with gstreamer: Frames from the camera arrive to python at the end of the pipeline as an appsink. The Gstreamer pipeline I configured via python was: src = Gst.ElementFactory.make("v4l2src") src.set_property("device", "/dev/video0") src.set_property("do-timestamp", 1) filt = Gst.ElementFactory.make("capsfilter") filt.set_property("caps", Gst.caps_from_string("video/x-raw,format=NV12,width=800,height=600,framerate=12/1")) p1 = Gst.ElementFactory.make("cedar_h264enc") p2 = Gst.ElementFactory.make("h264parse") p3 = Gst.ElementFactory.make("rtph264pay") p3.set_property("config-interval", 1) p3.set_property("pt", 96) p4 = Gst.ElementFactory.make("rtph264depay") p5 = Gst.ElementFactory.make("avdec_h264") sink = Gst.ElementFactory.make("appsink", "sink") pipeline_elements = [src, filt, p1, p2, p3, p4, p5, sink] sink.set_property("max-buffers", 10) sink.set_property('emit-signals', True) sink.set_property('sync', False) sink.connect("new-sample", on_buffer, sink) This pipeline definition causes a callback on_buffer to be called every time a frame is emitted from the camera: def on_buffer(sink: GstApp.AppSink, data: typing.Any) -> Gst.FlowReturn: # Sample will be a 800x900 byte array in a very frustrating YUV420 format sample = sink.emit("pull-sample") # Gst.Sample ... conversion to numpy array # rgb is now in a format that Pillow can easily work with # These two calls are what you compiled opencv for 1.5 hours for :-D rgb = cv2.cvtColor(img_arr, cv2.COLOR_YUV2BGR_I420) rgb = cv2.cvtColor(rgb, cv2.COLOR_BGR2RGB) Once you have a nice pillow RGB image, it's easy to pass this into a Tensorflow model, and there is tons of material on the web for how you can do things like that. For fast but not so accurate detection, I used the ssdlite_mobilenet_v2_coco pretrained model, which can handle about 0.5 frames per second per core of the H2 Allwinner CPU. There are some problems I still have to work out. Occasionally the video stream stalls and I haven't figured out how to recover from this without restarting the app completely. The way frame data is passed around tensorflow worker processes is probably not ideal and needs to be cleaned up, but it does allow me to get much better throughput using all four cores. For more details, including a detailed build script, the full source is here: https://github.com/atomic77/opilite-object-detect
-
Full root filesystem encryption on an Armbian system (new, fully rewritten, replaces my earlier tutorial on this topic) MMGen (https://github.com/mmgen) This tutorial provides detailed, step-by-step instructions for setting up full root filesystem encryption on an Armbian system. The disk can be unlocked remotely via SSH or the serial console, permitting unattended bootup. An automated script that performs the same steps, saving you much time and effort, can be found at https://github.com/mmgen/mmgen-geek-tools Note that unlike my earlier tutorial all steps are performed within a running Armbian system. The tutorial is known to work with the following board/image combinations: Orange Pi PC2 Debian Buster mainline / Ubuntu Bionic and Focal legacy RockPi 4 Debian Buster mainline / Ubuntu Bionic and Focal legacy RockPro 64 Ubuntu Focal mainline Odroid HC4 Debian Buster mainline / Ubuntu Focal mainline You may have success with other boards/images too. If so, please post the details below (or open an issue in the mmgen-geek-tools Github repository), and I’ll add your board to the list. Requirements: A SoC with a running, upgradeable and Internet-connected Armbian system A blank Micro-SD card and USB card reader, or, alternatively, a blank eMMC installed on the board The ability to edit text files and do simple administrative tasks on the Linux command line Step 1 - Preliminaries All steps in this tutorial are performed as root user on a running Armbian system (the “host”). The encrypted system (the “target”) will be created on a blank micro-SD card. If your board has an eMMC not currently in use, the system can be created on it instead. Architecture of host and target (e.g. 64-bit or 32-bit ARM) must be the same. For best results, the host and target hardware should also be identical or similar. Building on a host with more memory than the target, for example, may lead to disk unlocking failure on the target. If you’re building the target system for the currently running board and with the currently running image, which is the recommended approach, the two preceding points will be a non-issue. Packages will be installed using APT, so the host machine must be Internet-connected and its clock correctly set. Step 2 - Upgrade your system and install the cryptsetup package # apt update && apt upgrade # apt install cryptsetup Step 3 - Get and unpack the latest Armbian image for your board Create your build directory: # mkdir armbenc-build && cd armbenc-build Download the Armbian image of your choice for your board, place it in this directory and unpack: # xz -dv *.img.xz Step 4 - Create mount directories and set up the loop mount Create the mount directories: # mkdir -p mnt boot root Determine your first free loop device: # losetup -f Associate the image file with the loop device name displayed by the previous command. This will be '/dev/loop0' in most cases, but if your output was different, substitute that for '/dev/loop0' in the following steps. # losetup -P /dev/loop0 *.img Examine the disk image using fdisk on the loop device: # fdisk -l /dev/loop0 The output should look something like this: Device Boot Start End Sectors Size Id Type /dev/loop0p1 32768 3489791 3457024 1.7G 83 Linux Make a note of the start sector (32768 in this case). You’ll need this value in the steps below. Now mount the loop device: # mount /dev/loop0p1 mnt Step 5 - Copy the boot loader to the SD card Insert the blank micro-SD card and card reader into a USB port. Determine the SD card’s device name using 'dmesg' or 'lsblk'. We’ll assume it to be '/dev/sda', since that’s the most likely case. If your device name is different, substitute it for '/dev/sda' in the the following steps. For an eMMC, the device name will probably be '/dev/mmcblk1'. WARNING: if '/dev/sda' refers to some other storage device, running the following commands unchanged will destroy data on that device, so always remember to substitute the correct device name!!! The best way to eliminate this danger is to disconnect all unused storage devices on the board before proceeding further. Copy the image’s boot loader to the SD card, using the Start sector value from Step 4 as the argument for 'count': # dd if=$(echo *.img) of=/dev/sda bs=512 count=32768 Step 6 - Partition the SD card # fdisk /dev/sda At the fdisk prompt, create a new DOS disk label with the 'o' command. Use the 'n' command to create a primary partition of size +200M beginning at the same Start sector as the disk image. Type 'p' to view the partition table, which should now look something like this: Device Boot Start End Sectors Size Id Type /dev/sda1 32768 442367 409600 200M 83 Linux Use 'n' again to create another primary partition beginning one sector after the first partition’s end sector and filling the remainder of the card. Type 'p' once more to view the partition table: Device Boot Start End Sectors Size Id Type /dev/sda1 32768 442367 409600 200M 83 Linux /dev/sda2 442368 30636031 30193664 14.4G 83 Linux Ensure that the first partition’s Start sector matches that of the disk image (32768 in this example) and that the second partition’s Start sector is one greater than the End sector of the first (442368 and 442367, respectively, in this example). If you’ve made a mistake, use 'd' to delete a partition and start again. Once everything looks correct, type 'w' to write the partition table to disk. Step 7 - Copy the system to the SD card The following commands will create a filesystem on the SD card’s boot partition and copy the boot partition data from the image file to it. Don’t forget to substitute the correct device name if necessary. If you’re building the system on an eMMC, the boot partition device is likely to be '/dev/mmcblk1p1' instead of '/dev/sda1'. # mkfs.ext4 /dev/sda1 # or '/dev/mmcblk1p1', for an eMMC target # e2label /dev/sda1 CRYPTO_BOOT # mount /dev/sda1 boot # cp -av mnt/boot/* boot # (cd boot; ln -s . boot) Create the encrypted root partition. When prompted for a passphrase, it’s advisable to choose an easy one like 'abc' for now. The passphrase can be changed later with the 'cryptsetup luksChangeKey' command (type 'man cryptsetup' for details) once your encrypted system is up and running. # cryptsetup luksFormat /dev/sda2 # or '/dev/mmcblk1p2', for an eMMC target Activate the encrypted root partition and create a filesystem on it: # cryptsetup luksOpen /dev/sda2 rootfs # enter your passphrase from above # mkfs.ext4 /dev/mapper/rootfs Mount the encrypted root partition and copy the system to it: # mount /dev/mapper/rootfs root # (cd mnt && rsync -a --info=progress2 --exclude=boot * ../root) # sync # be patient, this could take a while # mkdir root/boot # touch root/root/.no_rootfs_resize Unmount the boot partition and image and free the loop device: # umount mnt boot # losetup -d /dev/loop0 Step 8 - Prepare the target system chroot # BOOT_PART=($(lsblk -l -o NAME,LABEL | grep CRYPTO_BOOT)) # ROOT_PART=${BOOT_PART%1}2 # ROOT_UUID="$(lsblk --nodeps --noheadings --output=UUID /dev/$ROOT_PART)" # BOOT_UUID="$(lsblk --noheadings --output=UUID /dev/$BOOT_PART)" # cd root # mount /dev/$BOOT_PART boot # mount -o rbind /dev dev # mount -t proc proc proc # mount -t sysfs sys sys Copy '/etc/resolv.conf' and '/etc/hosts' so you’ll have a working Internet connection within the chroot: # cat /etc/resolv.conf > etc/resolv.conf # cat /etc/hosts > etc/hosts If you’re using non-default APT repositories, you may need to copy their configuration files as well so that 'apt update' and 'apt install' will use them inside the chroot. Note that you can only do this if the host and target systems have the same distro/version. If that’s not the case, you’ll have to edit the target files by hand. # cat /etc/apt/sources.list > etc/apt/sources.list # cat /etc/apt/sources.list.d/armbian.list > etc/apt/sources.list.d/armbian.list If you’re using an apt proxy, then copy its configuration file too: # cp /etc/apt/apt.conf.d/*proxy etc/apt/apt.conf.d/ Step 9 - Edit or create required configuration files in the target system Perform the editing steps below using a text editor of your choice: Edit 'boot/armbianEnv.txt' so that the 'rootdev', 'console' and 'bootlogo' lines read as follows. If you’ll be unlocking the disk via the serial console, then use 'console=serial' instead of 'console=display'. Note that enabling the serial console will make it impossible to unlock the disk from the keyboard and monitor, though unlocking via SSH will still work: rootdev=/dev/mapper/rootfs console=display bootlogo=false Edit 'etc/initramfs-tools/initramfs.conf'. If your board will have a statically configured IP, add the following line to the end of the file, substituting the correct IP in place of 192.168.0.88: IP=192.168.0.88:::255.255.255.0::end0:off If the board will be configured via DHCP, then edit the DEVICE line as follows: DEVICE=end0 If host and target systems are both Debian buster, you may wish add some key modules to the initramfs to avoid a blank display at bootup time. The easiest way to do this is to add all currently loaded modules as follows: # lsmod | cut -d ' ' -f1 | tail -n+2 > etc/initramfs-tools/modules Retrieve the SSH public key from the remote unlocking host and copy it to the target: # mkdir -p etc/dropbear/initramfs # rsync yourusername@remote_machine:.ssh/id_*.pub etc/dropbear/initramfs/authorized_keys If you want to unlock the disk from more than one host, then edit the authorized_keys file by hand, adding the required additional keys. Create 'etc/crypttab': # echo "rootfs UUID=$ROOT_UUID none initramfs,luks" > etc/crypttab Create 'etc/fstab': # echo '/dev/mapper/rootfs / ext4 defaults,noatime,nodiratime,commit=600,errors=remount-ro 0 1' > etc/fstab # echo "UUID=$BOOT_UUID /boot ext4 defaults,noatime,nodiratime,commit=600,errors=remount-ro 0 2" >> etc/fstab # echo 'tmpfs /tmp tmpfs defaults,nosuid 0 0' >> etc/fstab Create the dropbear configuration file: # echo 'DROPBEAR_OPTIONS="-p 2222"' > etc/dropbear/initramfs/dropbear.conf # echo 'DROPBEAR=y' >> etc/dropbear/initramfs/dropbear.conf If the target is Ubuntu bionic, then a deprecated environment variable must be set as follows: # echo 'export CRYPTSETUP=y' > etc/initramfs-tools/conf.d/cryptsetup Set up automatic disk unlock prompt. Performing this optional step will cause the disk password prompt to appear automatically when you log in remotely via SSH to unlock the disk. Using your text editor, create the file 'etc/initramfs-tools/hooks/cryptroot-unlock.sh' with the following contents: #!/bin/sh if [ "$1" = 'prereqs' ]; then echo 'dropbear-initramfs'; exit 0; fi . /usr/share/initramfs-tools/hook-functions source='/tmp/cryptroot-unlock-profile' root_home=$(echo $DESTDIR/root-*) root_home=${root_home#$DESTDIR} echo 'if [ "$SSH_CLIENT" ]; then /usr/bin/cryptroot-unlock; fi' > $source copy_file ssh_login_profile $source $root_home/.profile exit 0 Save the file and execute the command: chmod 755 'etc/initramfs-tools/hooks/cryptroot-unlock.sh' Step 10 - Chroot into the target system, install packages and configure Now chroot into the encrypted system. All remaining steps will be performed inside the chroot: # chroot . Install the cryptsetup package and the dropbear SSH server: # apt update # echo 'force-confdef' > /root/.dpkg.cfg # apt --yes install cryptsetup-initramfs dropbear-initramfs # for a buster or focal image # apt --yes install cryptsetup dropbear-initramfs # for a bionic image # rm /root/.dpkg.cfg Make sure everything was included in the initramfs (all three commands should produce output): # lsinitramfs /boot/initrd.img-* | grep 'usr.*cryptsetup' # lsinitramfs /boot/initrd.img-* | grep dropbear # lsinitramfs /boot/initrd.img-* | grep authorized_keys Now regenerate your SSH host keys: # ssh-keygen -A Your work is finished! Exit the chroot and shut down the board: # exit # halt -p Insert your freshly written SD card into the board’s main SD slot (or, if the target is an eMMC, just remove the SD card from that slot) and reboot. Unlock the disk by executing the following command on your remote unlocking machine, substituting the correct IP address if necessary: $ ssh -p 2222 root@192.168.0.88 If you performed step 9.10 above, the disk password prompt should appear automatically after login. If not, you must enter the command 'cryptroot-unlock'. You may also unlock the disk from the target board’s console if you wish. Note, however, that certain disk images (RockPi 4 buster mainline, for example) might give you a blank display at startup, so you’ll have to enter your disk password “blindly”. This bug will hopefully be fixed in the future. If all went well, your root-filesystem encrypted Armbian system is now up and running!
-
Hi all, Maybe there are a lot people who got this working but for me was today the day. I buyed a time a go a cheap but fast NVME SSD from Aliexpress. The smallest one a 128GB. I have also a 512GB in my laptop and for the price they are really good. But i needed also a USB-NVME external housing. That is the Ugreen NVME 10GBps to USB adapter. In very short but i will explain more in the future. 1. Flash a MicroSD card with your favourite Armbian to the MicroSD. Update with sudo apt-get update. Also with a SSH session not a problem. 2. Place the USB disk in a USB 3.0 port of the Orange Pi. By the OrangePi 4 it´s the blue one on the top. 3. run the command lsusb 4. Notice the dev id. In my situation it´s 174c:2362 5. Run the command with off course your dev id. Notice the :u at the end that must be added. echo "174c:2362:u" | sudo tee /sys/module/usb_storage/parameters/quirks 6. Replug the USB drive. I see the activity led on the drive short flashing. 7. Run the following command sudo nano /boot/armbianEnv.txt 8. Add the dev id after usbstoragequirks and close and save the file. By my system is the complete row: usbstoragequirks=174c:2362:u,0x2537:0x1066:u,0x2537:0x1068:u 7. Logout and in with your root account! This is very important. With sudo is this not possible. 8. Open armbian-config. Select System->Update Bootloader-> Boot from SD, root from NVME/eMMC etc. 9. The tool will ask you the directory to the disk. Most of time is this standard correct. You get a question about the filesystem. Select EXT4. You get a warning that the disk would be erased. Click on Ok. 10. Wait patiently to finish 11. And without failures you could click reboot and boot from USB/NVME! By my is the Orange:Pi a lot faster! Booting, updating copy files. Everything. I am really happy with this!
-
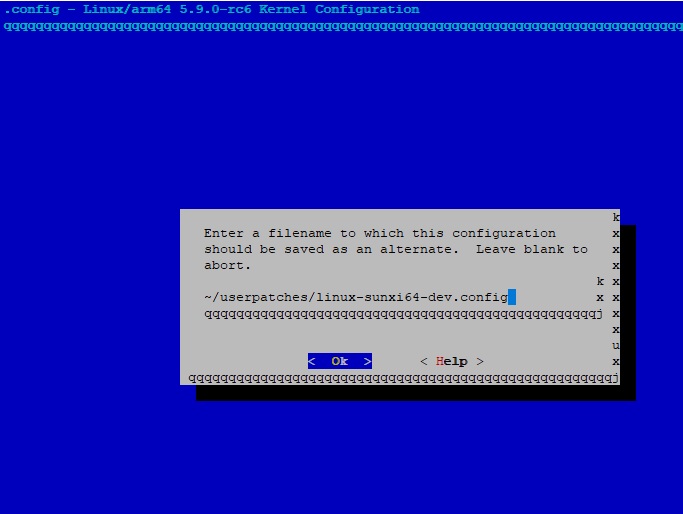
In this tutorial we build a custom .config for OrangePiOnePlus board, eg: to remove blutooth, WiFi and or USB3.x support since the hardware is not onboard, alternatively you can adjust settings to your needs which is not in the default .config. The section mentions, if file " userpatches/linux-$KERNELFAMILY-$KERNELBRANCH.config " exists, it will be used instead of default one from " config ". This means for the OPiOnePlus : " linux-sunxi64-dev.config " should be created, but please note "dev" is just one of the three options available, which are: " current ", " legacy " and " dev " The default config files are located in : " /armbian/config/kernel " and thus also holds a "linux-sunxi64-dev.config " config file. # #If user-provided kernel .config file IS NOT present yet # cd ~ git clone --depth 1 https://github.com/armbian/build armbian cd armbian ./compile.sh BRANCH=dev RELEASE=buster BUILD_MINIMAL=yes BUILD_DESKTOP=no KERNEL_ONLY=no KERNEL_CONFIGURE=yes EXTRAWIFI=no BOARD=orangepioneplus Yet rename ".config" and Save to " ~/userpatches/linux-sunxi64-dev.config " , find attached a screenshot # #If user-provided kernel .config file IS present # <script> cp -p ~/armbian/userpatches/linux-sunxi64-dev.config ~/ sudo rm -rf armbian git clone --depth 1 https://github.com/armbian/build armbian mkdir ~/armbian/userpatches cp -p ~/linux-sunxi64-dev.config ~/armbian/userpatches/ </script> Above can be scripted so you do not need to worry if for some reason you need to remove and rebuild your " armbian " directory from scratch Rest would be ( assuming your kernel has been customised to your needs ): cd armbian ./compile.sh BRANCH=dev RELEASE=buster BUILD_MINIMAL=yes BUILD_DESKTOP=no KERNEL_ONLY=no KERNEL_CONFIGURE=no EXTRAWIFI=no BOARD=orangepioneplus Hope this addition to user-provided-kernel-config explains the idea " in depth " . Happy configuring :-)
-
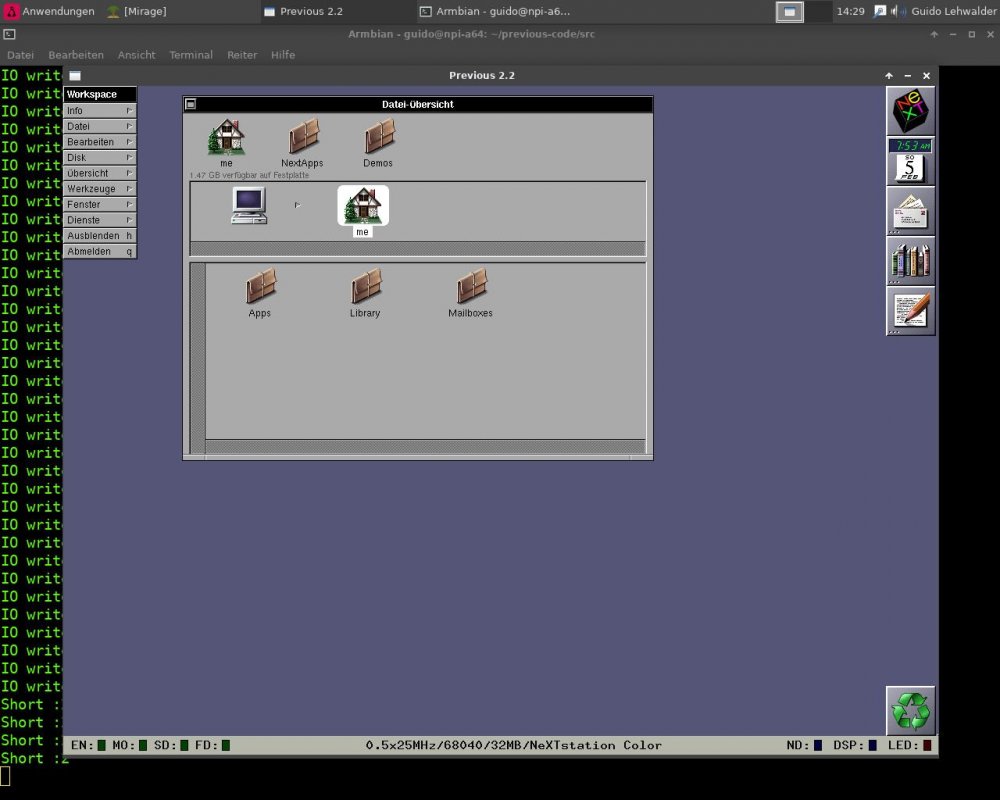
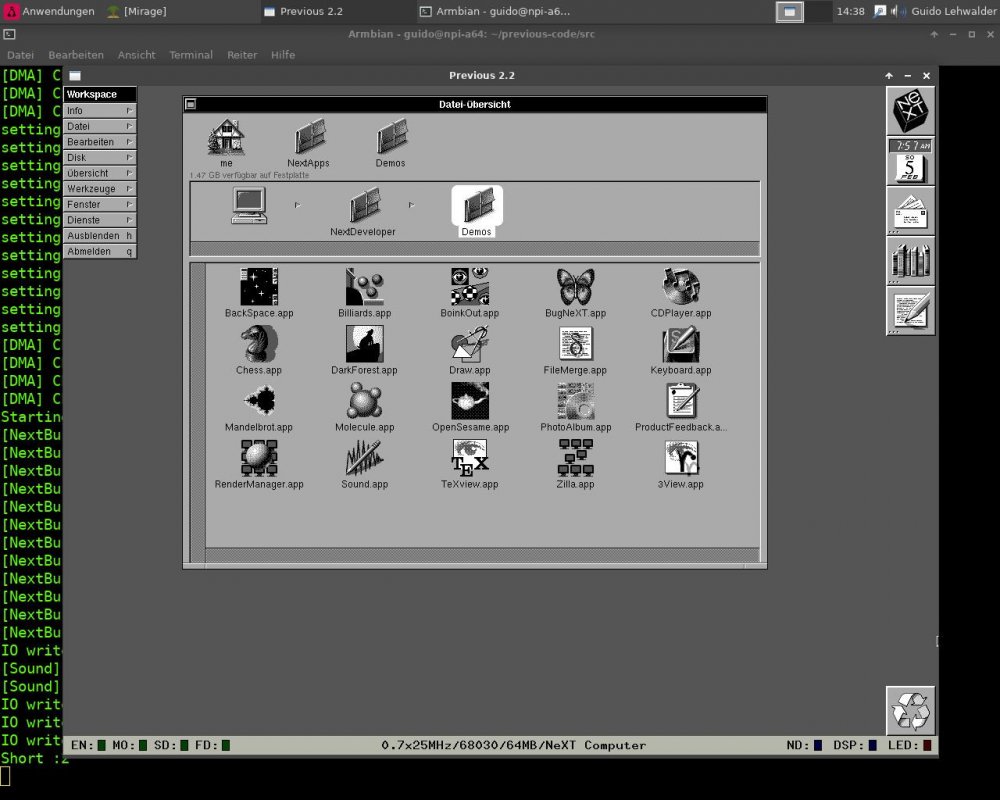
Today I did compile the NeXT-Cube/Station Emulator Previous 2.2 ( http://previous.alternative-system.com/index.php/build ) on my NanoPi A64 (with installed Desktop-option for using SDL) Installing the dependencies and compiling Previous 2.2 has been done with the follwing commands ( while compiling there were MUCH warnings ) : apt install zlib1g zlib1g-dev libsdl2-2.0-0 libsdl2-dev libpng16-16 libpng-dev libpcap0.8 libpcap0.8-dev apt install g++ cmake subversion cd /home/guido old Previous v1.8 : ===================== svn checkout svn://svn.code.sf.net/p/previous/code/branches/branch_realtime previous-code actual Previous v2.2: ===================== svn checkout https://svn.code.sf.net/p/previous/code/trunk previous-code cd previous-code ./configure make Run the program cd src ./Previous For booting the emulation you need a SCSI-HDD-dd-image of NeXTstep 3.3 You can get it at https://winworldpc.com/product/nextstep/3x inside the file Nextstep 3.3 HD Image With Previous The NanoPi A64 gets only 50-100% emulation speed of an original NeXT A little bit more while using a 68030 CPU and less on the 68040 CPU emulation. PS: because the emulator is using SDL for gfx you need to start the emulator from a graphical terminal on the NanoPi...